When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
What Are Keyloggers & How Can You Detect and Protect Yourself from Them? (All You Need to Know)
Read enough articles about cybersecurity and hackers, and you'll eventually come across this term - keyloggers.
Sounds pretty ominous, mysterious, and high tech, but what exactly is a keylogger, and how dangerous is it?
We'll tell you everything you need to know about them in this article - what they are, how people use them, how to detect keyloggers, and how to protect yourself from them.
What Are Keyloggers?
Keyloggers (also known as keystroke loggers) are programs that attach themselves to your operating system or Internet browser.
As the name implies, their goal is to log your keystrokes. They can be programmed to log everything you type, or just what you type in specific fields on specific websites (like the password field on PayPal).
Because of that, keyloggers are normally considered malware. They actually end up on your device through malware infections most of the time. They're not all malicious, though. Sometimes, they actually have legitimate uses (not that it makes it alright to use them).
How Do Keyloggers Work?
Let's keep it simple.
When you use a keyboard, your keystrokes get sent from it to your device. The keyboard's driver is responsible for translating the scan codes (the data from the keyboard) into letters, numbers, and symbols.
Thanks to that process, your operating system and any apps you use can understand your keystrokes.
Well, a keylogger positions itself into the receiving end of the translation process. So, it receives the translated keystrokes just like your OS and the apps you use do.
Software Keyloggers & Hardware Keyloggers
Most people are only familiar with software keyloggers - programs designed to record keystrokes that run in the background on your operating system.
Normally, whoever placed the keylogger on your device has remote access to it and the data it collects. They can configure the program to share data with them through emails, or website and database uploads. They can even program it to offer them a remote login to your device.
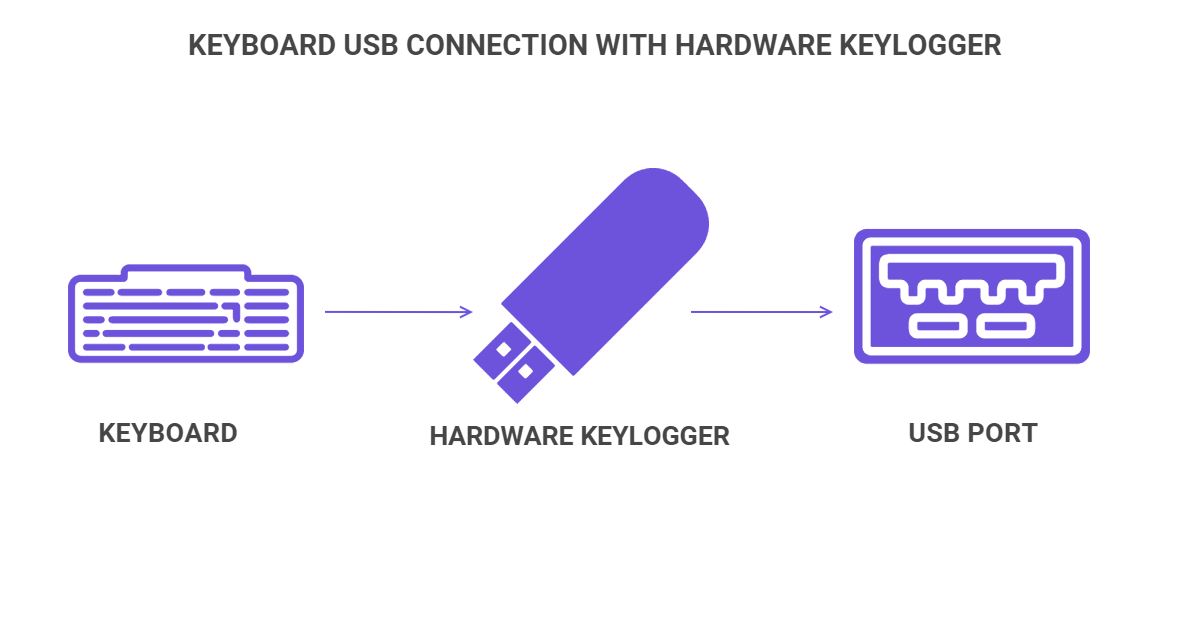
However, hardware keyloggers also exist. They're physical devices that do the same thing (log keystrokes). But you don't install them on an operating system. Instead, you physically place them on a device.
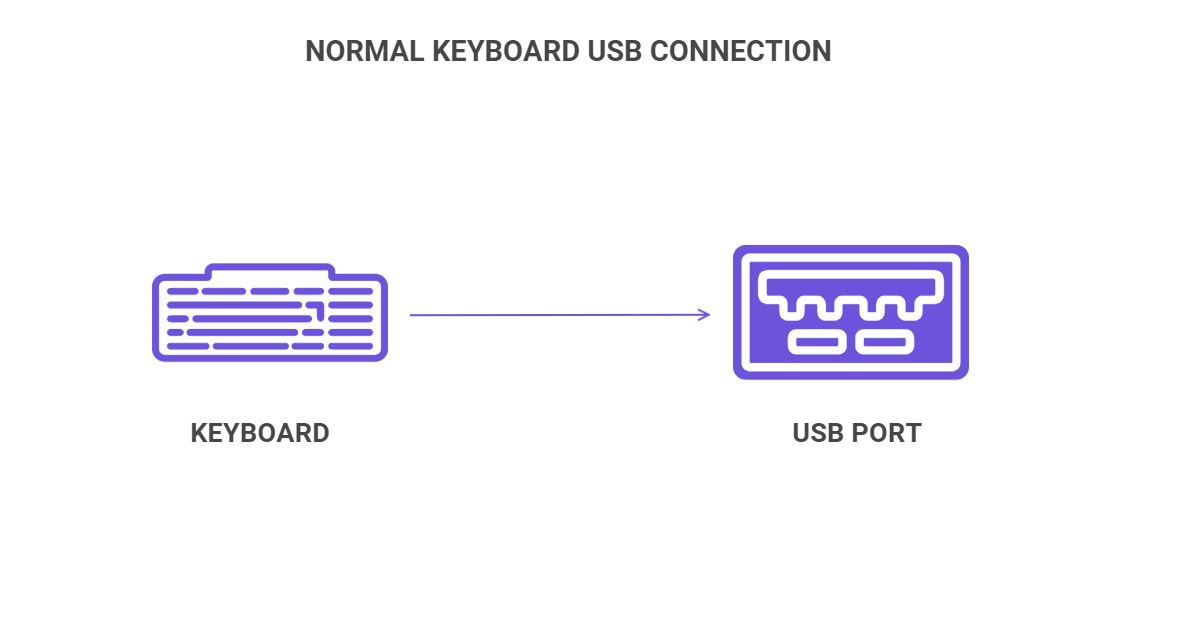
Most hardware keyloggers are placed where the keyboard cable connects to the device's USB slot. Right between them, to be exact.
So instead of this:
You'll have this:
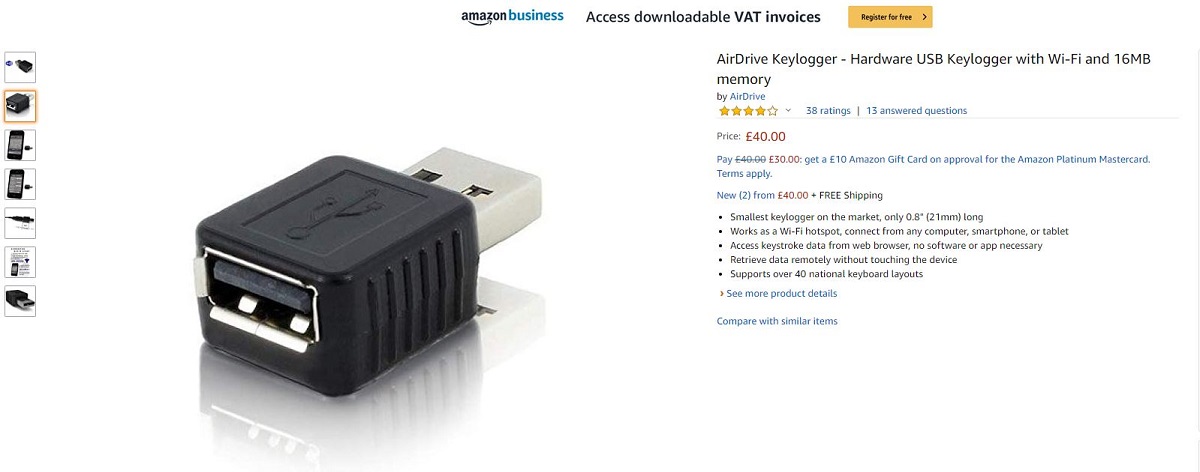
If you're having trouble picturing a hardware keylogger, here's an example:
Why Would Someone Use Hardware Keyloggers?
Because software can't detect them. Also, they don't rely on any software, so programming errors can't cause problems.
With older versions, the person using the keylogger has to go retrieve it from the device if they want to see the recorded data. But, nowadays, there are wireless versions that connect to a local WiFi network and send the logged keystrokes through emails.
Still, hardware keyloggers are obviously only useful if the target uses a desktop PC. With a laptop, the keylogger is pretty easy to notice.
Oh, and don't think that you're safe from hardware keyloggers just because you use a wireless keyboard. Many of them are vulnerable to the KeySniffer attack. While not exactly a hardware keylogger, it still allows an attacker to eavesdrop on your keystrokes if they're transmitted over unencrypted communication channels.
Besides that, there's also KeySweeper, a stealthy hardware keylogger that looks like a wall charger. It can passively sniff, decrypt, and log keystrokes from various wireless keyboards. Then, it send that data to an attacker over GSM. What's more, you can configure it to send data based on:
- Usernames
- URLs
- Trigger words
How Are Keyloggers Used?
For cyber attacks, right?
Yes, hackers employ keyloggers a lot. But they're not the only ones. Surprisingly, employers, family, and digital marketers might use keyloggers too.
Hackers
Keyloggers are invaluable tools for cybercriminals. It's how they often manage to compromise user accounts and company data.
Hackers usually spread keyloggers by:
- Triggering installs or activation when you click a link or open an attachment in a phishing email.
- Triggering installs or activation when you install a certain program.
- Using other malware (particularly Trojans) to infect devices with keyloggers.
- Exploiting vulnerable browsers through webpage scripts.
- Setting up fake websites, and using phishing messages or MITM attacks to get you to interact with them.
In some cases, cybercriminals can even program keyloggers to infect a network and spread to the devices connected to it. Or they can make it download and install other malware on a network.
Hackers might also set up hardware keyloggers at Internet cafes. Or a rogue employee could use one to steal valuable data from the business they work at.
And no, skilled cybercriminals aren't the only ones who use keyloggers. Even wannabe hackers who are still in high school can use hardware keyloggers to get their grades up.
Famous Keylogger Attacks
- Hackers used phishing and keyloggers to break into health insurer Anthem's servers in 2015.
- In 2016, researchers from RiskIQ (in collaboration with ClearSky) discovered that cybercriminals were using a web-based keylogger to compromise tons of popular eCommerce sites.
- In 2016, security researchers from Trend Micro found that hackers were using a commercial keylogger program (Olympic Vision) to hijack employee and executive accounts from companies in 18 countries across the US, Middle East, and Asia.
- A new malware strain called Virobot was discovered in 2018. Not only could it act as a keylogger, but it could function as ransomware and a botnet too.
- Hackers used keylogger malware in 2017 to breach The San Antonio Institute for Women's Health, San Antonio's largest OB-GYN.
Employers
Companies often use keylogging software to track their employees. It's called "corporate keylogging" and it's perfectly legal most of the time - as long as the keyloggers are only installed on the company's network and work computers.
Employers normally use software keyloggers. IT teams can configure them to detect keywords, and send real-time alerts whenever someone copies some files, enters sensitive values, or runs shady commands.
From the company's perspective, using keyloggers makes sense:
- It helps security teams notice insider threats.
- It helps HR managers and supervisors make sure employees meet their KPIs and don't slack off.
- And it also helps auditors check how well the business complies with laws and regulations. If someone inside the company violates them, keyloggers make it easy to locate that person.
Digital Marketers
Back in 2017, researchers from Princeton University found that roughly 482 websites from Alexa top 50,000 sites (so pretty popular websites) used web scripts that acted like keyloggers.
And the scripts didn't just record keystrokes, but mouse movements and scrolling behavior too!
Why would they do that?
Because it helps marketers gather behavioral data about you - how you interact with their sites, what ads interest you the most, what content you like and don't like, etc.
Besides that, IT teams, product managers and/or owners, and UX designers might also use keyloggers in their products to identify and fix user issues - usually during the onboarding process or closed BETAs.
Shady? Yes, but probably legal because they likely mentioned they do that in their ToS page. You know, the long piece of text full of lawyer talk you didn't bother to read (don't worry - most people don't).
To be fair, that reasoning makes sense because it helps companies offer a significantly more personalized user experience. But it doesn't make it any less creepy.
Jealous Spouses & Overprotective Parents
Husbands or wives worried their significant other is cheating on them, or helicopter parents who want to keep a close eye on their kids' online activities are likely to use keyloggers too.
No, we're not exaggerating. There are even online articles recommending the best keyloggers for monitoring children's social media activities.
Is it legal for them to do that?
It's hard to say. Using keyloggers is normally illegal in most countries. However, according to some divorce lawyer sites, it seems it might be technically legal to use them as long as you're "cautious."
Also, the article we linked above says you could use a keylogger if it's on a device you own. So that kind of makes it seem like it's alright for parents to do it (unless their kids have receipts proving they bought the devices).
How Dangerous Are Keyloggers?
Extremely dangerous.
A keylogger can help hackers get their hands on your login credentials, bank account details, credit card numbers, and personal information you might not want made public (sexual orientation, political beliefs, childhood trauma, psychological problems, medication, etc.).
If something like that would happen, a cybercriminal could:
- Empty your bank accounts.
- Max out your credit cards, ruining your credit score.
- Impersonate you online.
- Use knowledge of your personal secrets to blackmail you.
How to Detect Keyloggers
With hardware keyloggers, the solution is obvious - you need to check the device's ports to make sure there's no "extra" component between the keyboard's cable and the USB port.
With software keyloggers, though, things are a bit more complicated. But the good news is you might be able to detect them with the following solutions:
Task Manager (Windows) & Activity Monitor (Mac)
The Task Manager/Activity Monitor is a great way to check background processes. To start Task Manager on Windows, press Ctrl + Shift + Esc. And on Mac, you'll find Activity Monitor by going to Applications > Utilities. Alternatively, use Spotlight to find it.
Now, you need to find processes from apps you don't recognize. It's easier to do that on Windows 10 than Mac because the Task Manager clearly separates apps from background processes.
When you spot an app or process you've never seen or that just sounds shady, google its name. If you get results about keyloggers, congrats - you found the culprit.
Also, on Windows 10, make sure to check the Startup tab too. If the keylogger was programmed to activate when your OS starts up, you should find it there.
This isn't an ideal way of doing things, and it can be tedious. But it's worth going through it.
Internet Usage Reports
Since hackers can view the data their keyloggers collect remotely, it means the malware is communicating with them over the web. So, it should show up in your operating system's Internet usage report feature.
Basically, if you see any weird app you don't recognize using the web, google it to see if it's a keylogger or not.
On Mac, you can check that with the Activity Monitor. Just select the Network tab.
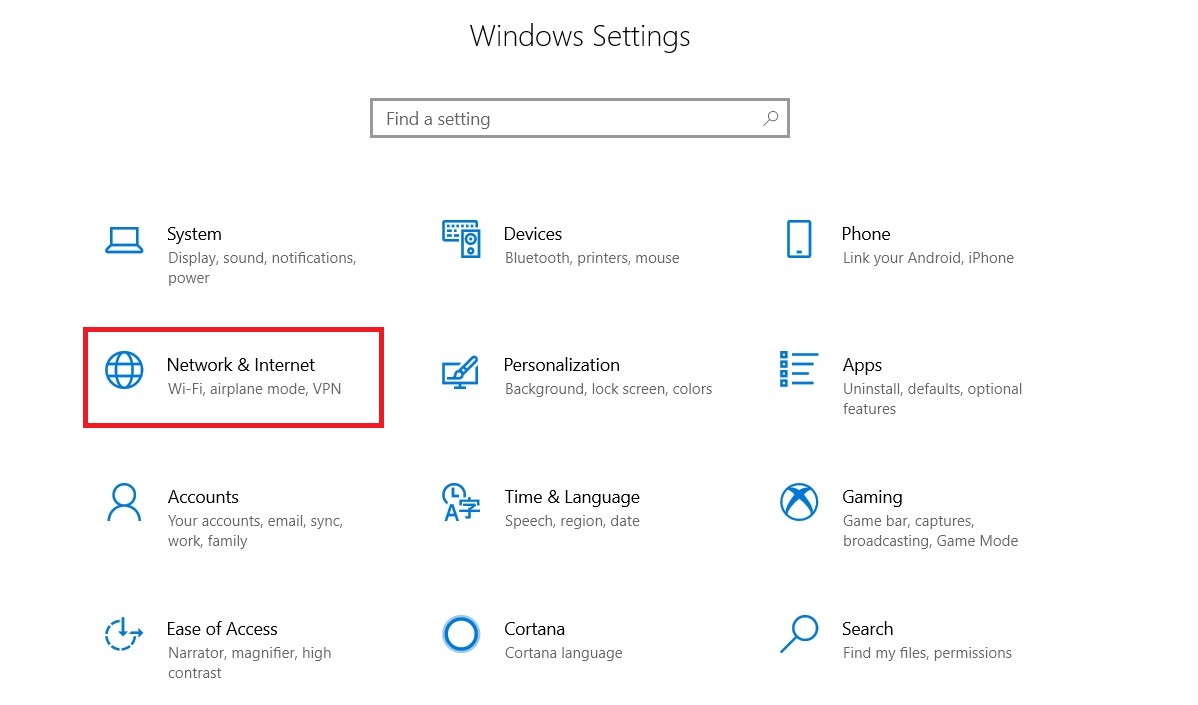
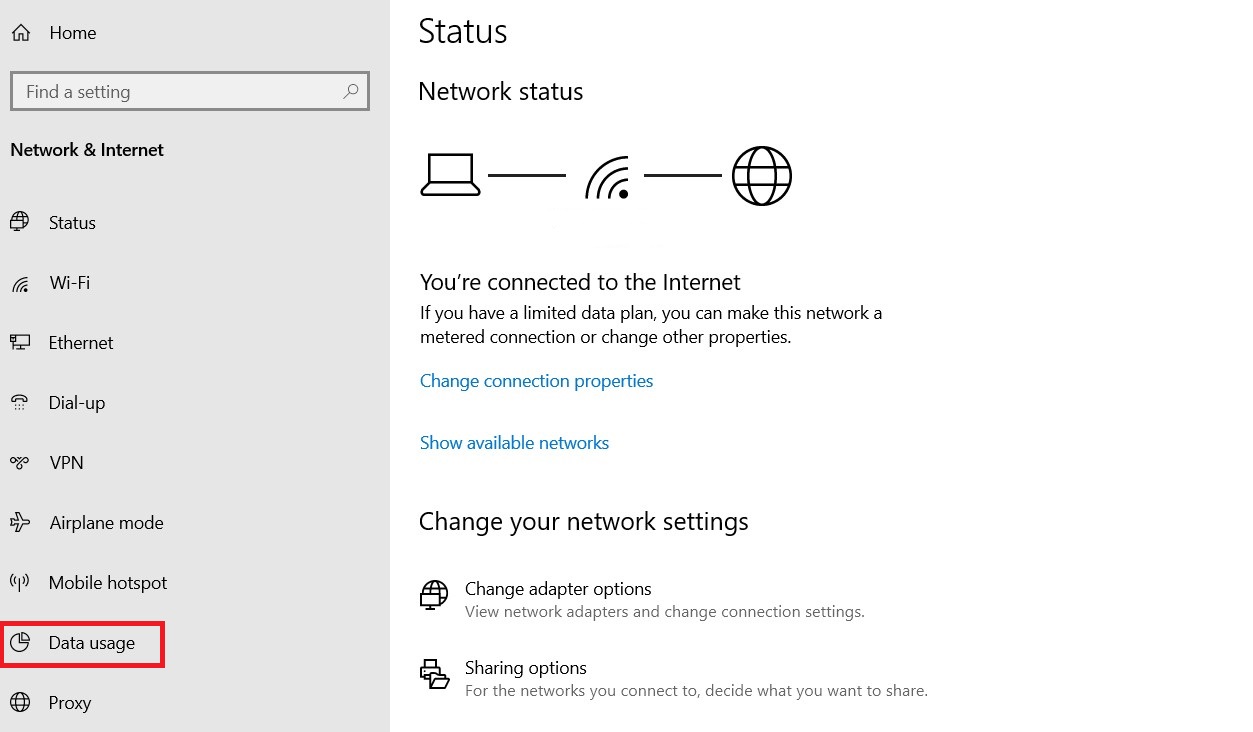
On Windows 10, you need to open up Windows Settings (Win button + I). There, select Network & Internet.
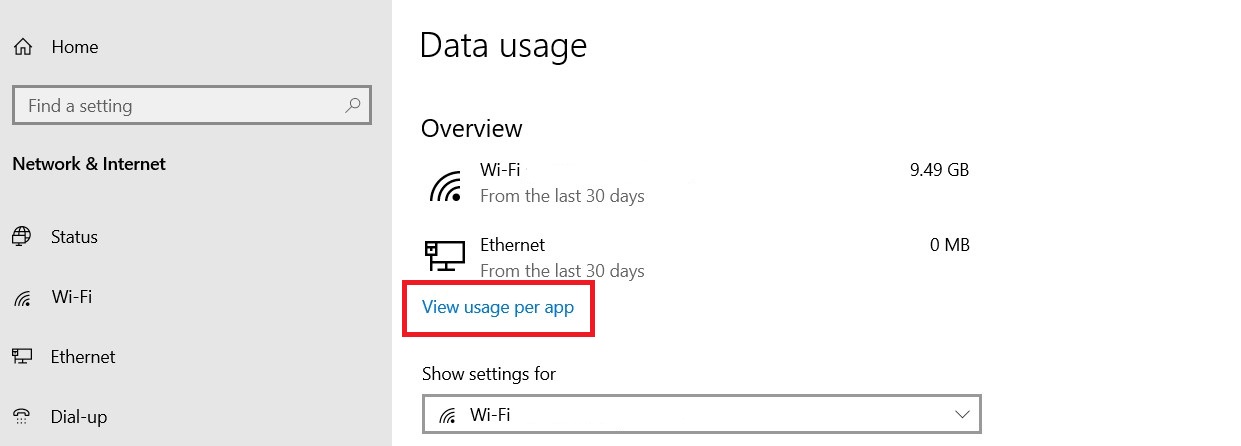
Next, click Data usage.
Under your web connections, hit View usage per app. Feel free to switch between networks if you want with Show settings for.
Browser Extensions
Hackers can sometimes hide keyloggers in your browser's extensions. So it's worth looking through them. If you see extensions you don't remember adding, disable and remove them.
Here's how to quickly check your extensions on most browsers:
- Chrome - Just type chrome://extensions in the URL bar and hit enter.
- Opera - Exactly like Chrome: type opera://extensions and hit enter.
- Firefox - Type about:addons in the URL bar.
- Microsoft Edge - Click Extensions in the browser menu.
- Internet Explorer - In the Tools menu, click Manage add-ons.
- Brave - Type brave://extensions in the address field.
- Vivaldi - Type vivaldi://extensions in the URL field.
- Safari - Click Preferences from the Safari menu, and choose Extensions.
- Yandex - Click Yandex Browser settings (the three-line icon) and select Add-ons.
Can a VPN Protect You from Keyloggers?
No, it can't. Software keyloggers act like malware, and VPNs aren't designed to protect your device at the hardware level. They can only encrypt your Internet traffic and "hide" your IP address by routing your connections to the web through a VPN server.
They can't detect, quarantine, and remove malware like antivirus software can. And obviously, VPNs can't do anything about hardware keyloggers.
That doesn't mean you shouldn't use a VPN at all, though. They can offer some protection (no matter how limited it is) in the form of blocklists.
Basically, they block your connections to shady websites. That might not sound like much, but consider this - many of those sites could be malicious, ready to infect your device with keyloggers (and other malware) at the click of a button.
CyberSec from NordVPN and CleanWeb from Surfshark are good examples of that kind of protection. If you'd like to learn more about those providers, check out our reviews (NordVPN and Surfshark).
Read More: What a VPN Does Not Do – Everything You Need to Know About Potential Misconceptions
Can Off-Screen Keyboards Protect You from Keyloggers?
They might, but not 100%.
Here's the thing - the on-screen keyboard uses a driver just like a regular keyboard. So a keylogger can exploit it to intercept the translated keystrokes sent to your operating system.
Even if that couldn't happen, don't forget that keyloggers are malware. And skilled hackers can program malware to do almost anything.
For example, they could configure a keylogger to take screenshots of your screen. Alternatively, they could make it capture an image of the area around your mouse pointer (so which letter you click on the on-screen keyboard).
How to Protect Yourself from Keyloggers
Here's a list of things you should try:
Use Antivirus Software
Keyloggers are malware - at least when hackers use it against you. Obviously, the best line of defense is antivirus software. They are security programs specifically programmed to protect your device against malware infections.
Just make sure you run regular scans (ideally each day) and keep the antivirus software up-to-date. If you skip an update, it might not be able to detect new strains of malware (including keyloggers).
Read More: TechNadu's Guide to the Best Antivirus Software
Enable 2FA/MFA on All Your Accounts
2FA stands for Two-Factor Authentication, and MFA means Multi-Factor Authentication. These are security settings that add an extra step in the login process.
Here's how it normally works - when you log in, you'll enter your username/email and password as usual. Next, you'll have to enter a randomly-generated code to complete the login process. The code is usually generated on your phone through an app (like Google Authenticator).
That way, even if cybercriminals would manage to steal your login credentials with keyloggers, they wouldn't be able to compromise your accounts. They would need direct access to your mobile device to do that.
Use Password Managers
A password manager is an online tool that secures your passwords in one place. Basically, it encrypts them, acting like a digital vault. You only need one master password to access and use them.
Password managers should offer some protection against keyloggers through their auto-fill features. Basically, you save sites you log into in your password vault, and then use a browser extension to automatically fill the login fields when accessing them. No typing needed.
Wait a minute, won't keyloggers compromise your master password, giving hackers direct access to all your passwords?
That can happen, which is why you should always enable 2FA/MFA on your account (like we already said).
Also, instead of typing your master password into the site, try copy-pasting it. Obviously, that implies storing it in a text file, so make sure you encrypt it, and keep it on an USB flash drive or an air-gapped device (no access to the web or connected to any network).
If you need help picking a really good password manager, check out our guide.
Use Script Blockers
These tools are the perfect way to protect yourself from hackers who use malicious scripts that act like keyloggers. Or marketers who use invasive scripts to monitor what you type on their websites or how you interact with their ads and copy.
uMatrix is by far the best tool for the job. It's open-source, free, and works on most browsers. It's a bit technical, yeah, but it can keep you safe from shady background scripts.
We also recommend using uBlock Origin. It mostly blocks ads, but it can be configured to block scripts too. And if you use it on Firefox, it will block cloaked first-party scripts. Plus, don't forget that hackers can use malicious ads to infect your device with keyloggers.
Use a VPN
Like we already said, a VPN won't protect you from keyloggers (or any kind of malware). But it can block connections to malicious sites, preventing hackers from infecting your device with keyloggers.
Also, VPNs might prevent cybercriminals from targeting you with MITM attacks that redirect you to phishing sites. A VPN encrypts your traffic, so a hacker can't use packet sniffers to monitor your data packets to see what sites you visit.
Without that information, they can't successfully redirect you to fake sites infected with keyloggers without making you suspicious.
For example, if you wanted to access google.com and got redirected to a PayPal-looking site asking you for your login credentials, you'd probably be on alert. You might even double-check the URL and see it's paipaI.xy.com instead of paypal.com.
So make sure you always use a VPN when you go online - at least when logging into accounts or making online payments.
If you need help picking a good VPN, we have you covered. Here's a list of the best VPNs on the market.
Keep Your Software Up-to-Date
Cybercriminals often abuse outdated apps and operating systems to inject devices with keyloggers. Basically, if you don't update apps or your OS, potential vulnerabilities will go unchecked.
So as tedious as updates can be (especially Windows updates), just bear with them. It's better to spend ten minutes waiting for updates to finish than to have a hacker compromise your accounts because your torrent client is still running the old version.
Practice Common Sense
Here's what we mean:
- Don't download files from sketchy websites - especially if they're advertised as free when the software is actually pretty pricey (like Adobe Photoshop).
- Don't open emails from unknown senders. Scammers could have sent them, and inserted malicious links or attachments that infect your device with keyloggers into them.
- If you visit a site, and are redirected to a different one, leave immediately. Don't spend any time on it, and definitely don't click any links or ads.
- If you ever see a random pop-up saying you won a new iPhone (or any other device or sum of money), ignore it and leave the site you were on. It's either a fake malicious website, or hackers compromised a legitimate site.
- Always double-check public computers. See if there's any extra hardware between the keyboard's cable and the computer's USB port. Also, avoid doing any sensitive stuff on public computers (like online banking, making payments, or checking your email).
Basically, don't fall for any phishing tricks. To learn more about that, check out our anti-phishing guide.
How to Get Rid of Keyloggers
Unfortunately, just running an antivirus scan isn't usually enough to get rid of keyloggers. Instead, you'll need specialized software (called anti-keyloggers). These tools perform in-depth audits of the processes on your device, checking pretty much everything:
- OS and BIOS processes
- Background apps and services
- Browser settings
- Network settings
- Plug-ins
They also check all the data they find against an extensive database of keylogger strains.
Besides them, you should also use anti-rootkits since many keyloggers are actually rootkits.
We'll go ahead and show you some of the best tools for getting rid of keyloggers.
Malwarebytes Anti-Rootkit
Malwarebytes is an extremely efficient anti-malware tool. So it only makes sense they'd have a very good anti-rootkit service too.
While their anti-rootkit tool is in Beta, it gets the job done pretty well. It performs in-depth scans against keyloggers and other kinds of rootkits at the core of your operating system (only Windows, for now).
And here's the best part - it's completely free.
SpyShelter
SpyShelter is a very efficient tool that runs silently in the background and automatically blocks keyloggers when they try to infect your device.
Their keylogger database is pretty extensive. So much so that their Anti KeyLogging Module can easily protect you from any keylogger strain (even unidentified ones).
While SpyShelter isn't free, it has a free 14-day trial. That should be enough to see if the tool is right for you.
If it is, you can buy the premium version for roughly $32-$33 per device. And here's the good news - it's a one-time payment, not a recurring monthly or yearly subscription.
Zemana
Zemana offers antimalware solutions, but they have a dedicated anti-keylogger service too. It's pretty good at what it does, and it also has an encryption enforcer (SSL) for credit cards, social security numbers, and login credentials.
Zemana's tool also offers ransomware protection and adware removal, which are nice bonuses. Their service runs in the background, and constantly scans everything you download for signs of malicious behavior.
The service has a free demo, and its premium version costs $41,99 per year for one device right now. Also, it's only available for Windows.
Ghostpress
Ghostpress is user-friendly tool that offers protection against keyloggers by hiding and manipulating your keystrokes. For example, it can intentionally delay the input speed to disguise your writing behavior.
Besides that, it can even keep you safe from keyloggers that take screenshots.
Unlike Zemana and SpyShelter, Ghostpress is 100% free. Again, it's only for Windows, but it doesn't support Windows 10 2004 May update for the screenshot protection feature yet.
What's Your Take on Keyloggers?
How widespread are they, and how much do you think hackers rely on them? Also, do you think corporate or marketing-driven keylogging is justified or not?
Go ahead and share your thoughts with us in the comments. Also, if you know other ways to avoid keyloggers, or tools to get rid of them, please tell us about them.