Old Excel Macro Tricks Resurface via the ‘Avaddon’ Ransomware
- Excel 4.0 macros are getting trendy again, as malicious actors realized they are stealthier than newer macros.
- Although nearly three decades old, XML macros are still working perfectly on the latest versions of MS Excel.
- The latest actors to exploit this are Avaddon ransomware groups, and one in particular that targets Italians.
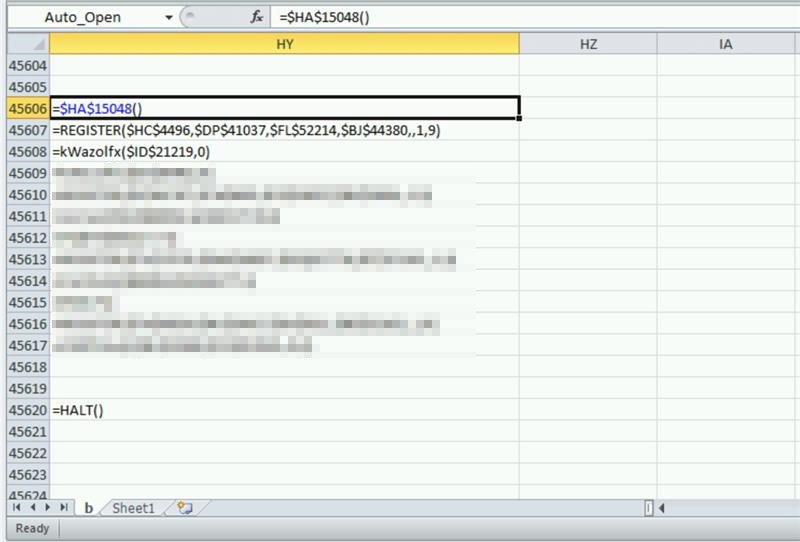
The ‘Avaddon’ ransomware has been very actively distributed in Italy lately, and researchers noticed that it exploits an old Excel 4.0 macros trick. The ransomware infection campaign that is still ongoing involves spamming people with messages of penalties and legal action being taken against their business due to “violations.” This apparently is enough to trigger the fear or curiosity of the recipient, who download the attached file. The thing is, though, the file isn’t a real notice, but a spreadsheet document laced with malicious Excel 4.0 macros that fetch the Avaddon ransomware.
Source: Bleeping Computer
Excel 4.0 macros are XML based, and they are harder to analyze compared to VBA macros that were rolled out with Excel 5.0 and are used ever since. Thus, actors are using these macros to trick anti-virus systems and bypass protection layers that may be in place. Excel 4.0 was released all the way back in 1992, almost 28 years ago, but its XML macros are still compatible with today’s Excel version and all versions in between. This is precisely why there has been an uptick in the deployment of Excel 4.0 macros by malicious actors lately, not just those who spread ‘Avaddon.’
We’re tracking a massive campaign that delivers the legitimate remote access tool NetSupport Manager using emails with attachments containing malicious Excel 4.0 macros. The COVID-19 themed campaign started on May 12 and has so far used several hundreds of unique attachments. pic.twitter.com/kwxOA0pfXH
— Microsoft Threat Intelligence (@MsftSecIntel) May 18, 2020
The Avaddon RaaS is currently recruiting more people to spread its otherwise robust ransomware tool, so numerous different tricks appear each day. Earlier reports presented different social engineering themes like sending emails with subjects like “Your new photo?” or “Do you like my photo?” and the attached JPG is actually a JavaScript downloader. That said, while staying informed about what is going on out there is key to your safety, being vigilant in general would be the best approach with any form of unsolicited communication. Avaddon actors will try out more alleys of infection, especially when their existing methods are exposed.
Source: How to Fix Guide
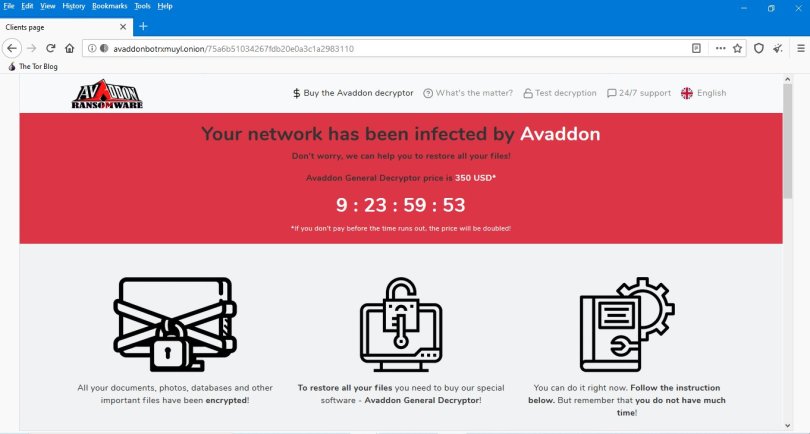
The Avaddon ransomware family appeared in early June 2020, and it seems to be a tool that was created from scratch in C++. It encrypts user data using AES-256 and RSA-2048, and the ransom demands generally range between $150 and $350, although some may go even higher. If your locked files carry the extension “.avdn,” you’ve been hit by this ransomware strain. At the moment, there are no working decryptors for Avaddon, so the best you can do is sign up for the “Notify Me” on ID Ransomware and get an alert as soon as an unlocking tool becomes available.