Powerline Networking Flaws Highlight a Fundamental Security Problem
- IBM warns about three critical unpatched vulnerabilities in PLC systems that are remotely exploitable.
- The flaws can result in the attackers taking full control of the target device, and even creating “denial of service” conditions.
- The vendor hasn’t responded to IBM’s notices and is unlikely to be preparing a patch at the moment.
IBM researchers have discovered multiple vulnerabilities in the Tenda PH5 Powerline extender kit, which brings the fundamental PLC security problem forward once again. More specifically, the X-Force Red team has discovered three critical flaws in the Tenda PA6 Wi-Fi Powerline extender, version 1.0.1.21, which could potentially allow a remote attacker to gain complete control over the target device. Since the system is using weak passwords by default, relying on the authentication step to ensure the security of these devices isn’t a realistic expectation.
These are the three vulnerabilities discovered by IBM’s hackers:
- Command injection by authenticated users (CVE-2019-16213)
- Post-authentication buffer overflow (CVE-2019-19505)
- Pre-authentication denial of service flaw (CVE-2019-19506)
Powerline communications became very popular after 2012, with the existing electric power infrastructure being also used to transmit internet data. It is a simple and reliable system that provides a solution mainly in areas of problematic coverage. As much as popular these kits have become, they remain a liability today, introducing remote attack risks for the devices that are connected to the internet through them.
Source: IBM
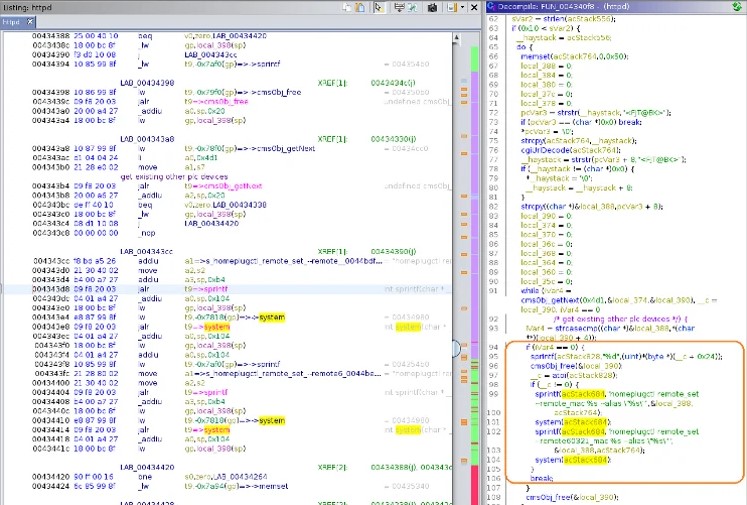
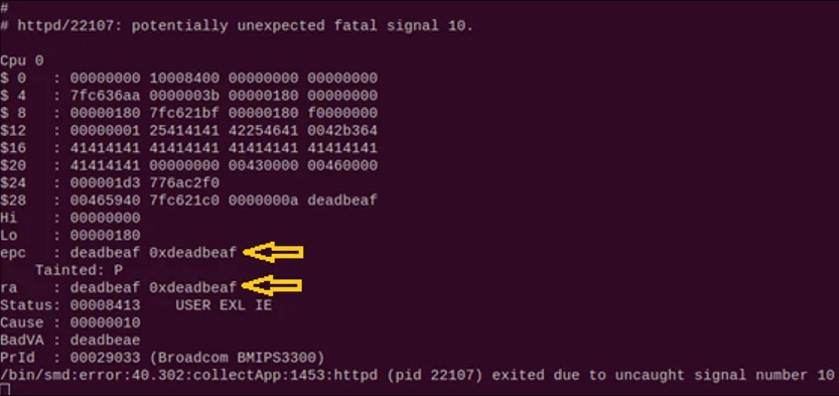
The first two flaws reside on a process named “httpd,” which is accessible in a web-UI that hides behind the “admin” password. This interface should normally be accessible only locally, but it can be exposed to WAN due to misconfigurations. The third flaw relies on “homeplugd,” a process listening on UDP port 48912. As no authentication is required for interaction with this service, a remote attacker could change AES data traffic encryption keys and put the device into a looping state.
Source: IBM
IBM found and confirmed the above flaws by developing a proof of concept code for each exploit, and the examples demonstrate that it’s pretty easy for skilled actors to take advantage of them. They then presented all details to Tenda, the vendor of the vulnerable kits, but they haven’t heard back from them yet. They may or may not be working on fixing patches, but the fact that they do not reply to any emails or phone calls isn’t leaving much margin for hope.
It means that the end-users have to undertake the device securing duties. Some common tips on that part would be to change the default passwords of your devices into something strong, update the device firmware by applying the latest available updates, and set up a firewall that limits access to web-based management interfaces for your routers. Finally, if the vendor no longer supports your router, replace it with a new model.