Phishing Actors Target “Office 365” Users Through Samsung and Oxford Servers
- Another phishing campaign focusing on Office 365 and the stealing of credentials has appeared.
- The actors have abused parts of the University of Oxford infrastructure to send the emails.
- The campaign is based on chains of redirections to help bypass security solutions.
Researchers have noticed an uptake in the targeting of “Office 365” and the abuse of mail servers, which increases the success of phishing campaigns. During the first week of April 2020, CheckPoint has recorded a large number of attacks that predominantly (90%) targeted Office 365 deployments, since more and more firms are adopting Microsoft’s solution. What’s particularly interesting is that we saw a very similar campaign in October 2019, and the fact that actors are still employing the same lure shows that it works.
Source: CheckPoint
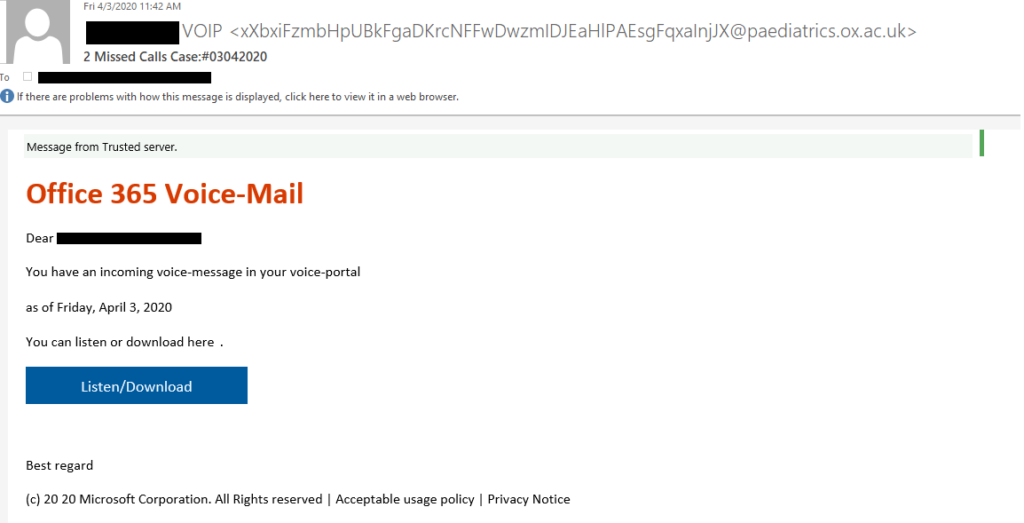
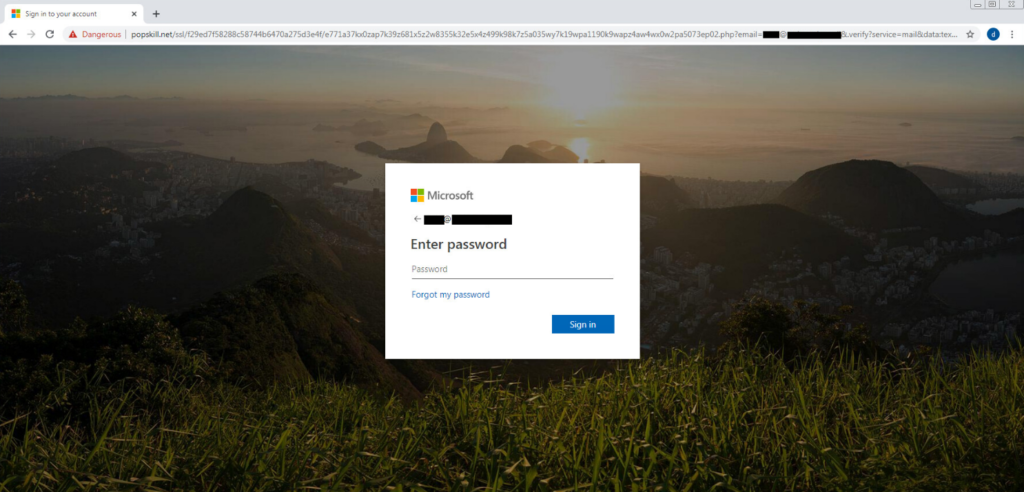
The actors send a phishing message claiming that the recipient had a voice message which they missed. To listen or download this message, the victims are prompted to push an embedded button that will supposedly take them straight to their Office 365 account. As expected, if the recipient clicks on this button, they are redirected on a spoofed Office 365 login page, following a two-stage redirection process. The first step attempts to use the legitimate domain of the target firm, and the second leads to a compromised WordPress site. In the most noteworthy cases spotted by CheckPoint, a Samsung domain (“samsung[.]ca”) was used in this step, while Adobe and the University of Oxford in the UK were also targeted. In 49% of the cases, the targets were based in Europe.
Source: CheckPoint
The University of Oxford wasn’t only a target in these campaigns but also an involuntary and ignorant collaborator. The phishing actors compromised subdomains belonging to the university’s various departments and found a way to abuse one of their SMTP servers. From there, they sent much of the phishing email volume to others, after they passed it through a NordVPN IP address to hide their tracks. This step ensured that the mails would reach the intended inboxes, rather than failing to pass reputation checks and ending up in spam.
Source: CheckPoint
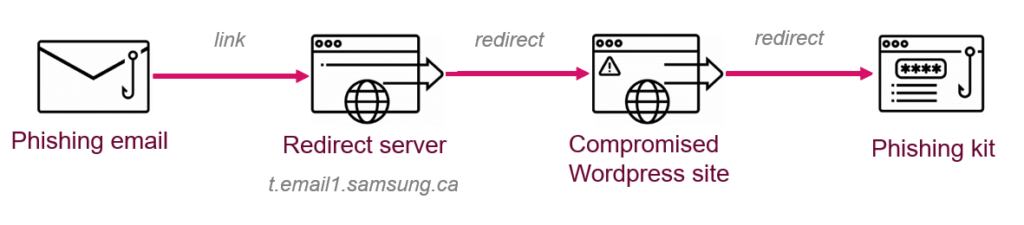
The fully-obfuscated phishing page was located in various WP sites and domains, and the victim ended up there via a chain of redirects. Simultaneously, the actors focused greatly on making this chain as optimized as possible in the duration of the campaign. The discovered redirection servers are given in the following list:
- t.email1.samsung[.]ca/r/
- t-email1.ottawashowers[.]ca/r/
- t-email1.instantytpresence[.]com/r/
- flycloud.co[.]il/r/
- cosmos.org[.]in/r/
- iyak.org[.]tr/o/
- ankit-gupta.co[.]in/r/
- istern.co[.]il/r/
One solid way to stay protected against these otherwise “basic” phishing attempts would be to deploy cloud and mail security solutions. If you have fallen victim to this campaign, you should consider your protection systems to be weak and inadequate.