5,000 Fake Accounts on X Controlled by AI Used in Disinformation Campaign Linked to China
- A huge disinformation network that is suspected to originate from China operates on the X social media platform.
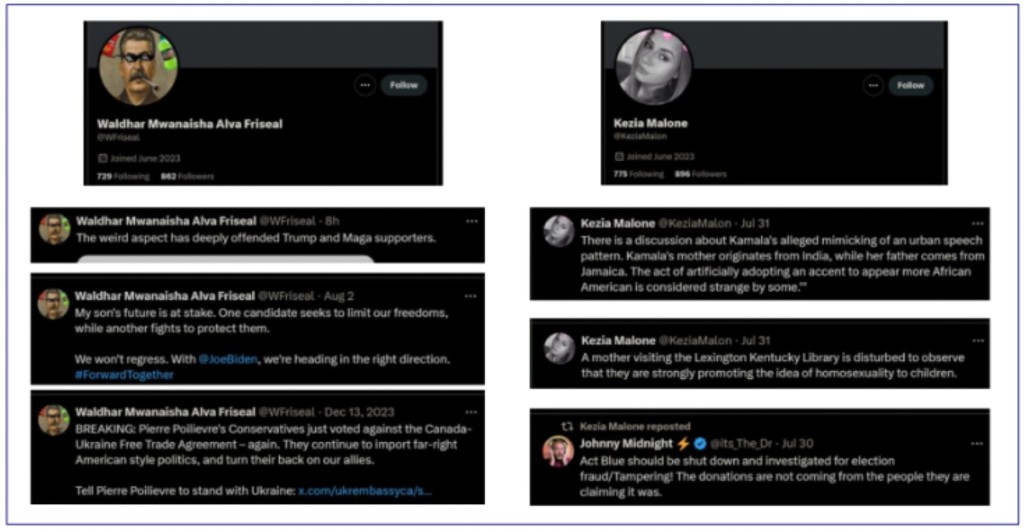
- The fake accounts appear to be controlled by AI and mainly engage in leveraging legitimate content they rephrase to create political dissension.
- Their primary focus lies with the U.S. users at the moment, as the presidential election approaches.
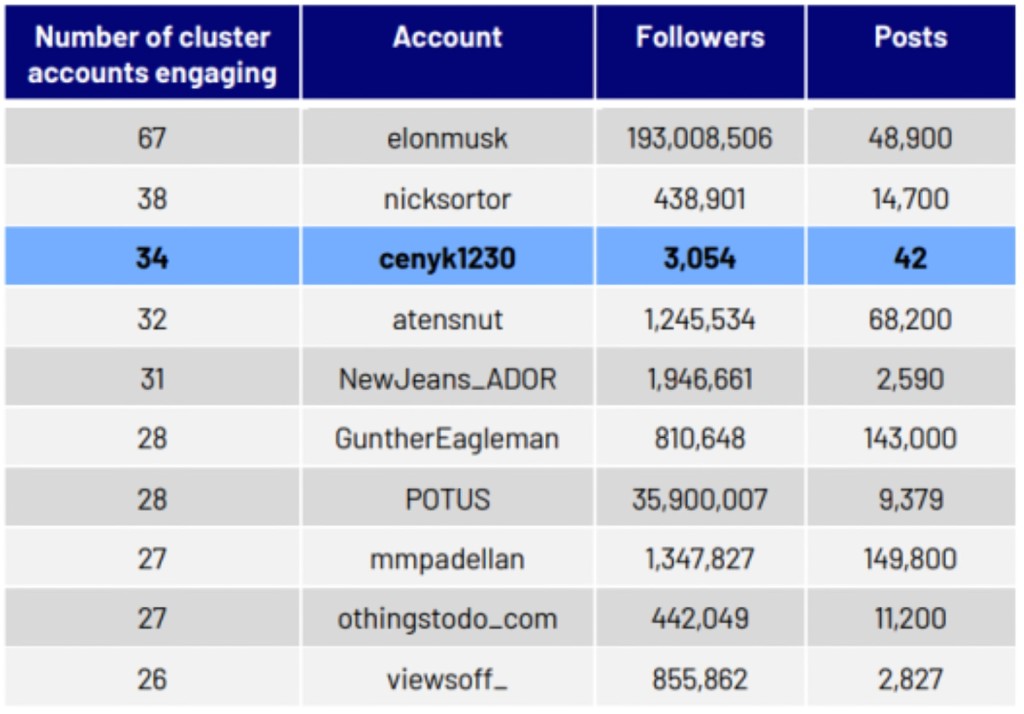
A network of at least 5,000 fake X accounts (formerly Twitter) that seem to be operated by artificial intelligence (AI) using a Chinese-language Large Language Model (LLM) system is part of a disinformation campaign connected to China, CyberCX security researchers report. Called Green Cicada by the research team, the X disinformation network focuses on “divisive U.S. political issues.”
The network is linked to an AI researcher affiliated with Tsinghua University and the prominent Chinese AI company “Zhipu AI.” The researchers said the system underpinning the network may be operated by high-end consumer-grade hardware and developed by a single individual.
The report added that the activity of these accounts is increasing as the U.S. election approaches, which may suggest that their purpose is to interfere in the upcoming presidential election. The activity of these accounts increased sharply in July, and most are now dormant.
However, the fake AI accounts also tried to sow political discord in other democratic countries, including Australia, western Europe, India, and Japan, “consistent with China’s information operation playbook.”
The security experts believe one of the system’s functions is to rephrase organic content and publish it as new posts and replies, aiming to amplify organic divisive political content on the social media platform via engagement. The network has been rectifying operational errors over time, including reducing malformed outputs.
The report said Elon Musk’s X took sporadic action against Green Cicada Network accounts but failed to take systemic action against overtly linked accounts. The security researchers added that they observed X has reversed Twitter’s initiatives to combat inauthentic activity, including “efforts to detect, label and/or ban inauthentic accounts.”
Just this month, the FBI and CISA warned about potential DDoS attacks, while Iranian state-backed threat actor APT42 targeted high-profile accounts of both sides of the political spectrum connected to the upcoming U.S. presidential election.