Over 5% of All Circulated Monero Reported to Be Mined Using Malware
- According to a research report submitted at Palo Alto research, over 5% of the Monero cryptocurrency in circulation has been mined using malware.
- The research accounts for only traditional mining hardware and not in-browser mining, which could raise the number much higher.
- Monero is currently the most popular cryptocurrency currently and over 500,000 malware samples have been found during its coin mining operations.
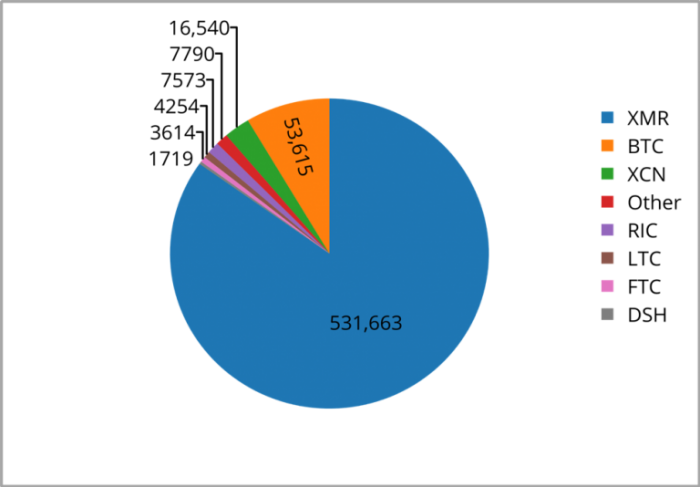
Over 5% of all Monero cryptocurrency in circulation has been mined using malware according to a research report submitted by Palo Alto Networks. The research included coin mining activities only using traditional mining hardware and not in-browser mining activities. The research firm analyzed 629,126 malware samples and it included 531,6663 malware samples that were focused on mining Monero which accounts for 84% of all samples.
The research team at Palo Alto discovered because malware needs to be built directly into the source code of cryptocurrency mining pool. The malware also requires a Monero address under which it operates and handles any illegal funds generated from mining the cryptocurrency. Most of the money has been tracked down by the research time through querying nine mining pools that account for 2,341 Monero addresses. All of the information regarding the illegal mining activities including the amount of money each Monero address generated has been uncovered.
Image Courtesy of Palo Alto
According to the report over $108 million has been generated from the illegal mining operations account for 798,613.33 XMR out of the 15,962,350 XMR in circulation. The malware was run by botnets to automate the process on infected devices. The botnets were able to generate $30,443 each day on infected devices at a hash rate of 19MH/s.
The people behind the malware have been reported to hold a very little amount of money in their digital wallets with 45% of the wallets connected to the malware showing a balance of $2.20 or less. The team at Palo Alto suggest that it could be the result of a failed malware, or simply the case of attackers being careful not to let themselves be traced back through high-value cryptocurrency wallets. A large amount of the operational insights of Monero cannot be accounted for with only around 20% of the total hash rate of XMR being publicly accounted for.