Over 360 Million Stolen Accounts Were Leaked for Free on Telegram
- Telegram combo lists and 361 million email addresses have been leaked for free via thousands of Telegram channels.
- The emails have now been added to the Have I Been Pwned (HIBP) data breach notification service.
- The owner of the service said a staggering number of these had never been seen in HIBP’s database before.
The “Have I Been Pwned” data breach notification service has added a huge set of 361 million unique email addresses, 151 million of which have never been on its site before. An anonymous security researcher sent Troy Hunt, the owner of HIBP, 122GB of data containing 1,700 files with 2B lines scraped out of several Telegram cybercrime channels.
The HIBP website allows you to check whether your email has been involved in data breaches. These emails came from credentials stolen via password-stealing malware, credential-stuffing attacks, and data breaches. Hunt said he has conducted some checks, and the new data appears to be legitimate.
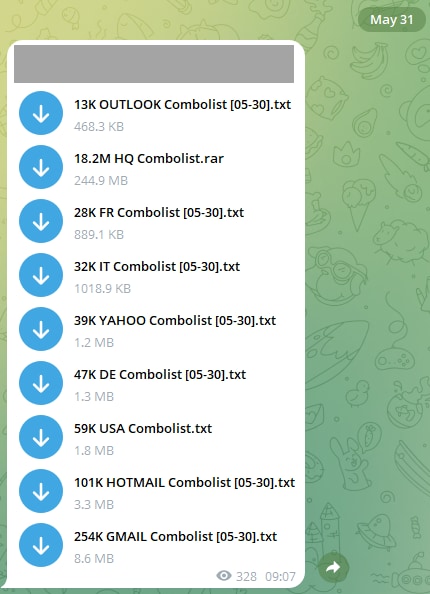
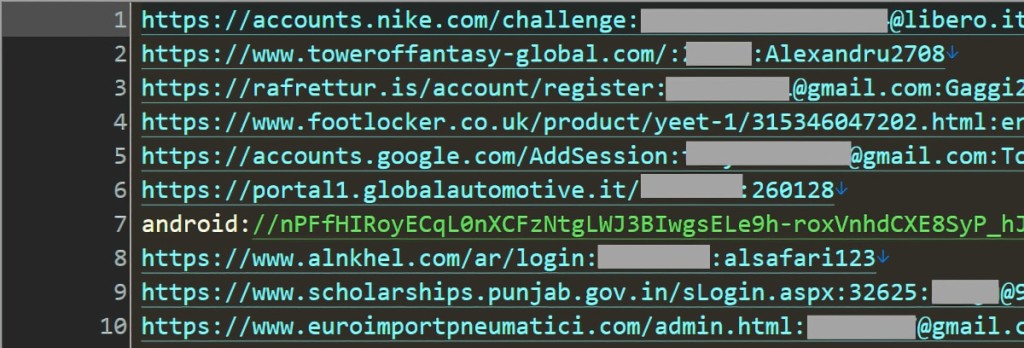
Data posted to Telegram channels comes as combinations of email addresses or usernames and passwords, usually referred to as "combo lists." The email addresses are accompanied by associated passwords and sometimes the website where they were stored and used for authentication, including Nike, Footlocker, Epic Games, and more.
These lists are often used by cybercriminals to gain mass access to accounts via credential stuffing. Hunt said he received 1,748 separate files last week. The data he received was scraped from 518 different channels, and while some files contained 0kb of data, others offered gigabytes of data.
Considering the massive dataset, verifying the legitimacy of all the leaked credentials is impossible. However, Hunt confirmed several leaked email addresses were correctly associated with the website in the lists by checking a few samples via password reset forms on the respective websites.
The Web security consultant also approached two hundred rows of stealer logs regarding one email address he'd never seen in a breach before, concluding the email owner’s device might have been infected with keyloggers.