3,300 Individuals Linked to Child Abuse Websites Were Exposed via Infostealer Logs
- Security researchers used malware data to track down individuals connected to child abuse websites.
- Infostealer logs can reveal granular data that can then be used by law enforcement.
- This led to over 3,300 unique credentials for known child abuse material websites being exposed.
Approximately 3,300 consumers of child sexual abuse material (CSAM) were singled out via the analysis of infostealer malware data from February 2021 to February 2024, a Recorded Future's proof-of-concept (PoC) report said.
Recorded Future's Identity Intelligence analyzed infostealer malware logs to identify CSAM, access additional sources, and reveal geographic and behavioral trends in CSAM communities. This information can help law enforcement understand CSAM website infrastructure and identity concealing techniques and identify potential consumers and producers.
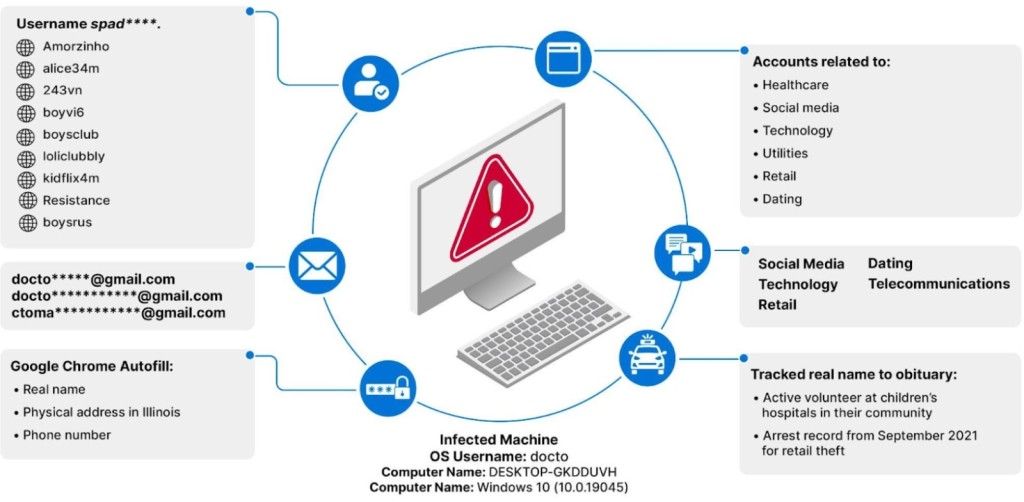
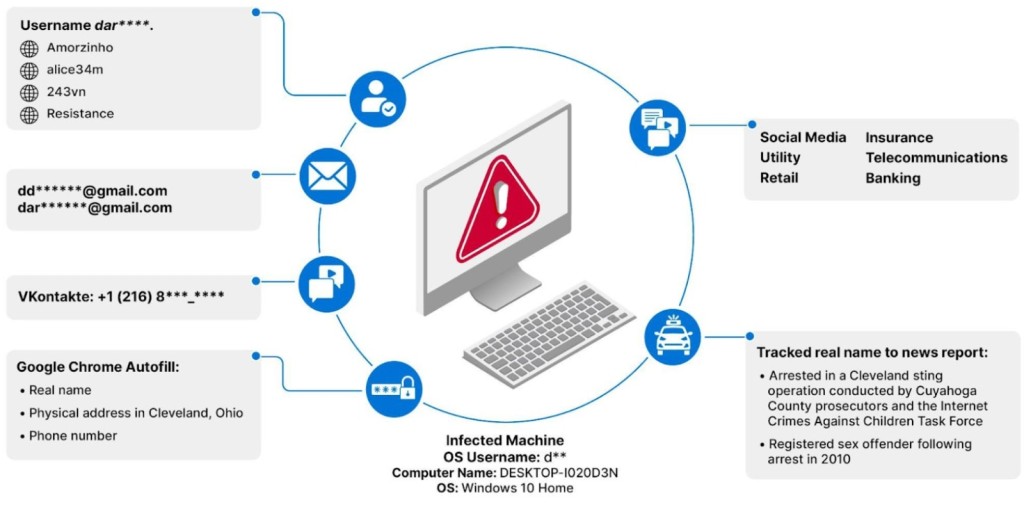
The analysis revealed 3,324 unique credentials used to access known CSAM websites and granular data, including their usernames, IP addresses, and system information. Of these, 4.2% had credentials for multiple sources.
The security researchers used the collected data to identify users who owned credentials to a previously made list of known high-fidelity CSAM domains, adding the help of non-profit organizations like the World Childhood Foundation and the Anti-Human Trafficking Intelligence Initiative (ATII).
For instance, individuals and their cryptocurrency addresses were identified via infostealer logs data and open-source intelligence (OSINT).
Infostealer malware is a tool usually deployed via phishing, spam, fake browser updates, SEO poisoning, and malvertising. Cybercriminals use it to exfiltrate sensitive user information such as usernames and passwords, card data, cryptocurrency wallet details, operating system information, browser cookies, screenshots, and autofill data.
Tor-based websites with .onion domains offer anonymity that enables CSAM production and consumption, although only a small percentage. Yet, most Dark Web browsing activity targets these websites.