Over 300,000 PCs of Bitcoin and Ethereum Users Infected with Malware
- Over 300,000 PCs of Ethereum and Bitcoin users have been infected by a malware according to Qihoo 360 Total Security.
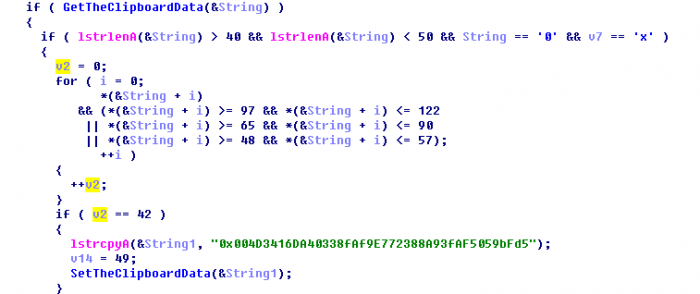
- The malware is being called ClipboardWalletHijacker, and it replaces strings in clipboards of computers.
- ClipboardWalletHijacker can be exploited to hijack Ethereum and Bitcoin transactions and transfer funds to attackers’ cryptocurrency wallets
A new form of malware has been discovered by Qihoo 360 Total Security that has infected over 300,000 computers owned by Bitcoin and Ethereum users. The malware can hijack Bitcoin and Ethereum wallet addresses of users and replace their wallet addresses of the malware’s author. Over $800 (0.12434321 BTC) has been hijacked across eight transactions successfully by the malware, and currently, security firms are pushing patches to clean the malware from systems.
The malware being dubbed as ClipboardWalletHijacker by the security firm is not the first of its kind. Similar malware that replaces bitcoin wallet strings to dupe unsuspecting users have been seen in the past, and it is recommended that users who deal in cryptocurrency transactions cross-check their wallet strings when pasting their addresses using Windows’ clipboard feature. Most of the infected PCs are from China and neighboring countries according to security firm Qihoo 360 Total Security.
Image Courtesy of Qihoo
Qihoo has been actively identifying multiple instances of malware related to crypto. The security firm also identified another malware dubbed TaskHostMiner that affected PCs owned by cryptocurrency holders. Over 10,000 PCs were said to be affected in a single day, and the malware can mine cryptocurrency on all infected systems. To ensure users are not able to catch onto the malware running in the background, it closes itself whenever the Windows Task Manager is opened by users. The WagonlitSwfMiner is a similar malware but is distributed via Adobe Flash and automatically installs mining software in the victim’s PCs.
Qihoo also discovered the Bondat IoT/Linux worm which affects web servers and IoT devices. A hidden cryptocurrency miner is placed in infected devices which can be used to brute-force WordPress websites and run the miner in the servers. It is quite difficult to track the Bondat IoT/Linux worm, requiring updated security plugins. With many WordPress users not updating plugins or enabling security measures, it is possible that multiple WordPress users are still affected by the malware.