250+ Google Play Decoy Apps Used in ‘Konfety’ Ad Fraud Hide Malicious Doppelgangers
- An ad fraud campaign uses over 250 decoy apps distributed via the Google Play store.
- Threat actors set up mediation SDK companies and spread the SDK to abuse respected publishers.
- The original malicious apps deployed via malvertising campaigns even masquerade as the decoys.
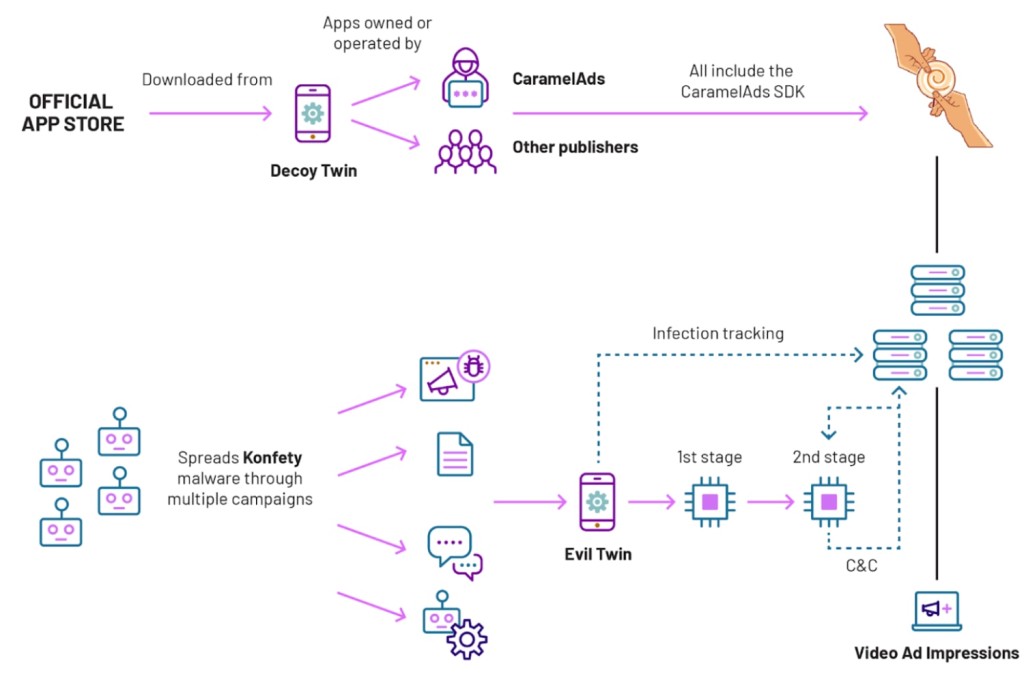
Cybercriminals exploited the Russia-based ad network CaramelAds mediation software development kit (SDK) for fraud targeting Android devices and employed an “evil twin” evasion method, a Satori report says. The campaign's (codenamed Konfety) abuse of the mobile advertising SDK makes it harder to distinguish malicious and legitimate traffic.
They put over 250 harmless decoy apps in the Google Play Store and distributed their respective "evil twins" via malvertising, click-baiting, and drive-by attacks for ad fraud, monitoring Web searches, installing browser extensions, and sideloading APK files.
The decoys behave normally, have GDPR consent notices, and most do not even render ads. Although they appear to be owned by different developers, many are template-based games mostly owned by the Konfety actors.
The fraudsters created a stripped-down version of the SDK without GDPR consent to produce these malicious twin apps that fraudulently generate ads via the publisher accounts from the Google Play Store apps.
The Konfety malvertising campaign apparently promotes APK mods and other software like Letasoft Sound Booster, which come with malicious URLs that redirect to domains where the malicious twin app can be downloaded – attacker-controlled domains, compromised WordPress sites, and other platforms, such as Docker Hub, Facebook, Google Sites, and OpenSea, which permit file upload.
The app icon is then hidden, and a second-stage DEX payload serves out-of-context, full-screen video ads while the user is on their home screen or using another app.
The malicious apps can spoof the decoys’ app IDs and advertising publisher IDs to render ads operating on the same infrastructure. They can also weaponize the CaramelAds SDK to visit websites using the default Web browser, sending notifications to users that ask them to open malicious links.
They can also sideload custom versions of other advertising SDKs. Once installed, the malware apps exfiltrate user search data via a search toolbar widget the Android user is asked to add to the device's home screen. The stolen data is sent to domains named vptrackme[.]com and youaresearching[.]com.