20M OpenAI Accounts for Sale, Leak Associated with Redline, StealC, Lumma, Vidar Infostealers
- The recent OpenAI credentials leak originated from infostealer malware infections, not a breach of OpenAI’s systems.
- The stolen credentials were part of a larger dataset scraped from private and public data leaks.
- These were associated with various infostealer malware families such as Redline, RisePro, Lumma, and StealC.
The OpenAI credential leak that a threat actor insinuated was for sale on a hacker forum originates from infostealer malware campaigns rather than a breach of OpenAI systems, according to investigations by the cyber intelligence firm KELA.
To verify the claim regarding OpenAI credentials, KELA analyzed a sample of 30 authentication details tied to “auth0.openai.com,” which the actor offered as proof, against a robust database of over 1 billion compromised accounts.
The credentials were sourced from an amalgamation of private and public datasets tied to infostealer malware operations. Notably, these credentials originated from 14 distinct sources, including both paid subscription services and public data leaks.
The most significant source—a private leak—encompassed over 118 million credentials cataloged in KELA’s data lake.
Multiple malware families were linked to these infections, with Redline, RisePro, StealC, Lumma, and Vidar identified as the primary infostealer variants used. The sample spanned infection periods from October 12, 2023, to July 28, 2024, with the bulk occurring between January and April 2024.
Additionally, KELA confirmed the credibility of 23 of the 28 email addresses in the sample, which were reused across multiple platforms, further verifying their validity.
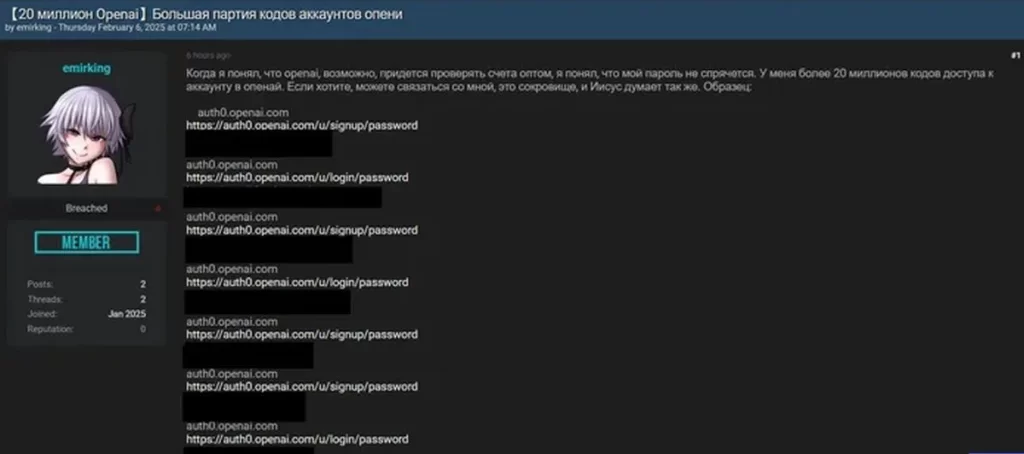
On February 6, 2025, a Russian cybercriminal operating under the alias “emirking” claimed to sell access to over 20 million OpenAI account credentials via a hacker forum. The post has since been deleted, though the actor remains active on the popular breach platform.
Their first recorded activity on the forum dates back to January 9, 2025, in a post claiming access to 50,000 compromised logs, listing sample data—including URLs, login credentials, and passwords. Despite the significant claims, both posts by emirking received minimal engagement, leaving their credibility and operational sophistication undetermined.