202 Million Chinese Jobseekers Resumes Exposed in a MongoDB Database Leak
- For the second time in less than a year, a MongoDB database suffered a data leak.
- Over 200 million users registered at 58.com were affected between December 23-28.
- The data leak was discovered by Bob Diachenko from HackenProof.
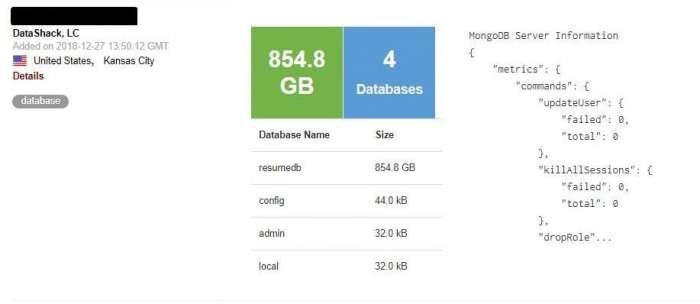
Ukraine-based security researcher Bob Diachenko discovered an unsecured MongoDB database server that contained resumes of over 202 million Chinese users. The US-based database was publicly accessible from December 23 to December 28 and was taken down soon after. Over a dozen IP addresses downloaded the data using an online scraping tool.
Diachenko, who is known for discovering prominent data leaks stated “each of the 202,730,434 records contained the details not only on the candidates’ skills and work experience but also on their personal info, such as mobile phone number, email, marriage, children, politics, height, weight, driver license, literacy level, salary expectations and more.”
Image Courtesy of HackenProof
This is not the first time a MongoDB database has been leaked. Diachenko was responsible for identifying another data leak last year that exposed data of over 11 million Yahoo! users. The current database leak was spotted by the security researcher when he found a scraping tool that had its source code posted on GitHub.
The MongoDB database contains data from 58.com which is a job portal for hundreds of millions of users. 58.com has acknowledged that data was leaked using a third-party scraper. However, a staff member revealed that resumes were not leaked unless the users manually set resume visibility to the public. The stolen data can be misused to make fraudulent financial transactions and put affected users at risk.
Canadian-based security researcher Huo Ju revealed that the job applicants affected by the MongoDB database leak could have the data used against them by attackers who are capable of finding more social relationship data by comparing the victims’ education and work experience. This is the second time that a MongoDB database has been affected by a data leak that has left millions of users concerned about their privacy.
What do you think about the MongoDB data leak? Let us know in the comments below. Also, to get instant tech updates, follow TechNadu’s Facebook page, and Twitter handle.