15 Million Trello Accounts Stolen via Open API Endpoint Were Leaked Online
- The cybercriminal who advertised the sale of over 15 million Trello accounts in January has leaked the data.
- An unsecured API endpoint seems to be the way the individual managed to collect the user information.
- The API was meant to help developers in their queries for details on member profiles.
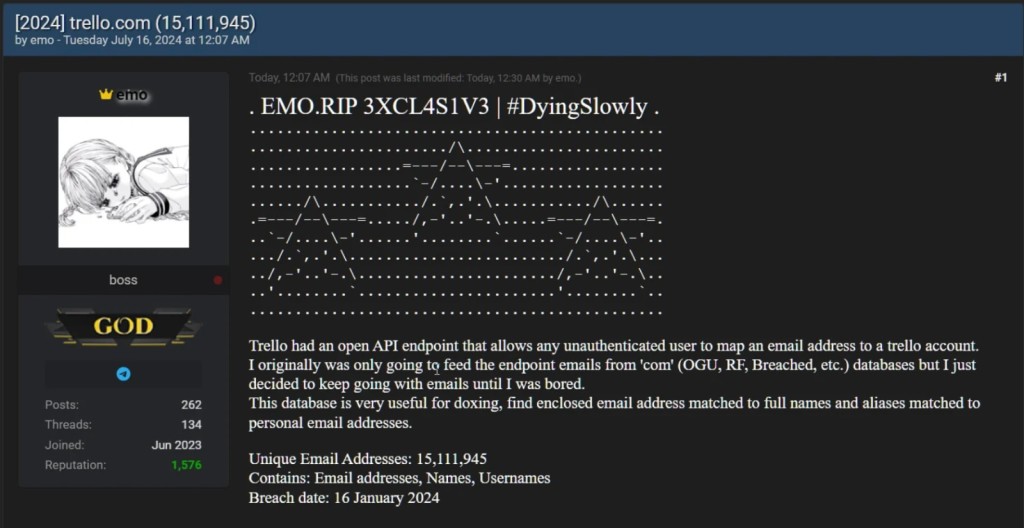
A threat actor known as 'emo' announced the sale of 15,115,516 Trello members’ accounts on a popular hacking forum in January. The hacker decided to leak the dataset on July 16, which includes email addresses, users’ full names, and public Trello account information.
The cybercriminal allegedly disclosed abusing an unsecured REST API that helped developers to request public information about a Trello profile based on users' ID, username, or email address, as per BleepingComputer.
Emo created a list of 500 million random email addresses, which were then verified against Trello account emails, and combined the results with the obtained account information to put together over 15 million user profiles.
The email addresses with associated full names and nicknames matched to personal email addresses make this database useful for doxxing, as these details help to potentially identify, locate, and contact these users.
Atlassian, the owner of Trello, recently confirmed this information and said unauthenticated users/services can no longer request another user's public information by email.
Earlier this month, the infamous ShinyHunters cybercriminal group allegedly leaked 33 million phone numbers related to Twilio-owned Authy on a hacking forum via the data breach of the two-factor authentication app they own. Hackers were able to verify the phone numbers of Authy users by exploiting an unsecured API endpoint.
Another recent API endpoint exploit is the now-patched CVE-2024-37032 Ollama vulnerability, which permitted unauthorized remote code execution. Insufficient validation on the server side of the Ollama REST API enables a potential attacker to send specially crafted HTTP requests to the Ollama API server, which is publicly exposed in Docker installations.