120 Vulnerabilities in LTE/5G Core Infrastructure Threaten City-Wide Cellular Disruption
- Several critical flaws in the LTE and 5G core infrastructure could cripple cellular communication in an entire city.
- The security issues concern city-wide monitoring, subscriber targeting, and core network compromise.
- Some of the discovered vulnerabilities enable remote exploitation through buffer overflows or memory corruption errors.
LTE and 5G alleged critical flaws were discovered by security researchers, who say 119 vulnerabilities exist across seven LTE and three 5G implementations – within Open5GS, Magma, and OpenAirInterface for both and within Athonet, SD-Core, NextEPC, and srsRAN only for LTE.
Alarmingly, each implementation tested in a comprehensive Florida Institute for Cybersecurity Research security analysis, both open-source and proprietary, was found to be vulnerable, raising systemic security issues that threaten the stability of cellular networks globally.
These vulnerabilities pose risks to national security and public safety. Every identified vulnerability can be leveraged to disrupt cellular communication city-wide, impacting phone calls, text messaging, and data connectivity.
Using only a small, malformed data packet sent as an unauthenticated user, an attacker could crash key network components such as the Mobility Management Entity (MME) in LTE or the Access and Mobility Management Function (AMF) in 5G.
The resulting service disruption could persist indefinitely, depending on how long operators take to identify and address the specific vulnerability.
Some of the discovered vulnerabilities enable remote exploitation (RCE) through buffer overflows or memory corruption errors, allowing threat actors to gain a foothold in the cellular core.
An attacker could track the location and connection data of all subscribers, conduct focused attacks on specific mobile devices, and escalate attacks to critical core components, such as the Home Subscriber Service (HSS) in LTE or Unified Data Management (UDM) in 5G, to execute nationwide service disruptions.
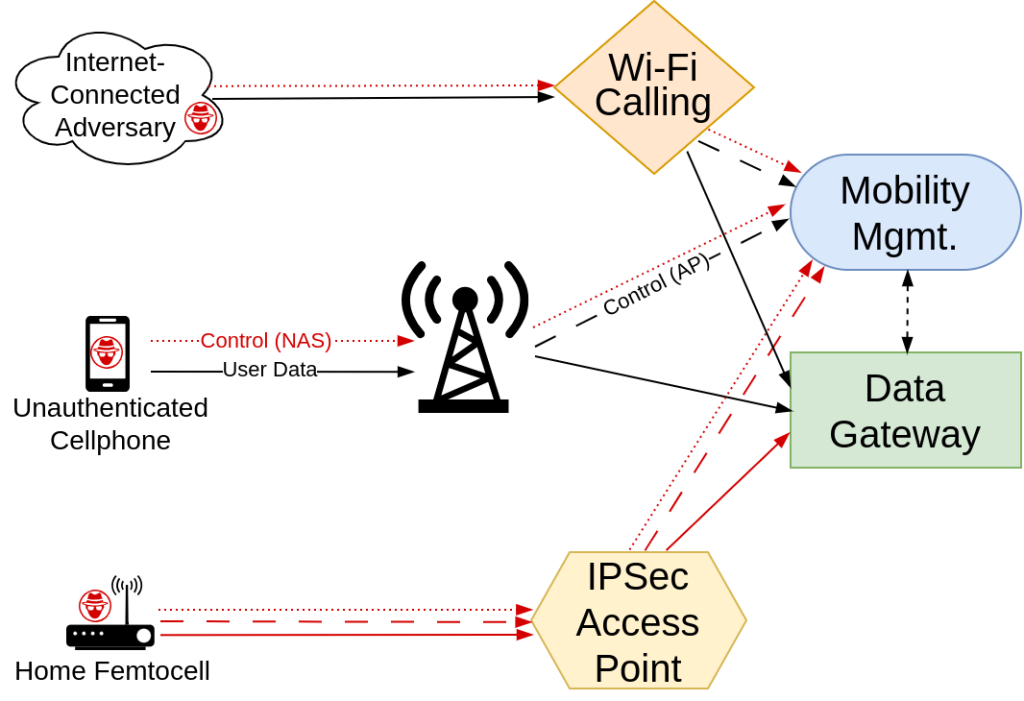
The research team demonstrated a proof-of-concept (PoC) RCE exploit targeting SD-Core to prove the feasibility and severity of such attacks. The security report presents two core threat models: unauthenticated device attacks and base station-level access.
The first model includes vulnerabilities exploitable by any unauthenticated mobile device, as the attacker doesn’t require a valid SIM card, only the capability to send specifically crafted packets using software-defined radios (SDRs).
Traditionally, such attacks required proximity to the target LTE/5G core (within radio range). However, the rise of Wi-Fi Calling services now extends this threat model to attackers connected via the internet, requiring only packet injection to exploit the network remotely.
The second model involves flaws accessible to attackers with base-station-level access to the cellular core—achieved by compromising base stations/femtocells or accessing an IPsec network due to misconfigurations or key leaks.
This model is realistic given the widespread availability of femtocells for home or office use, which act as base stations. Modern 5G base stations, located at easily accessible locations, further amplify the threat of physical compromise or key extraction via RAM/flash memory dumps.
In other news, Kiberphant0m claimed responsibility for breaching at least 15 telecommunications companies, as shared via posts on Telegram.