$10M Reward for Six Iranian Security Officials Linked to US Water Utilities Cyberattacks
- The U.S. offers a $10 million reward for six security officials linked to an Iran-based hacking group.
- The individuals are allegedly responsible for the cyberattacks on U.S. water utilities in 2023.
- They are believed to be part of the CyberAv3ngers hacker group, affiliated with Iran’s Islamic Revolutionary Guard Corps.
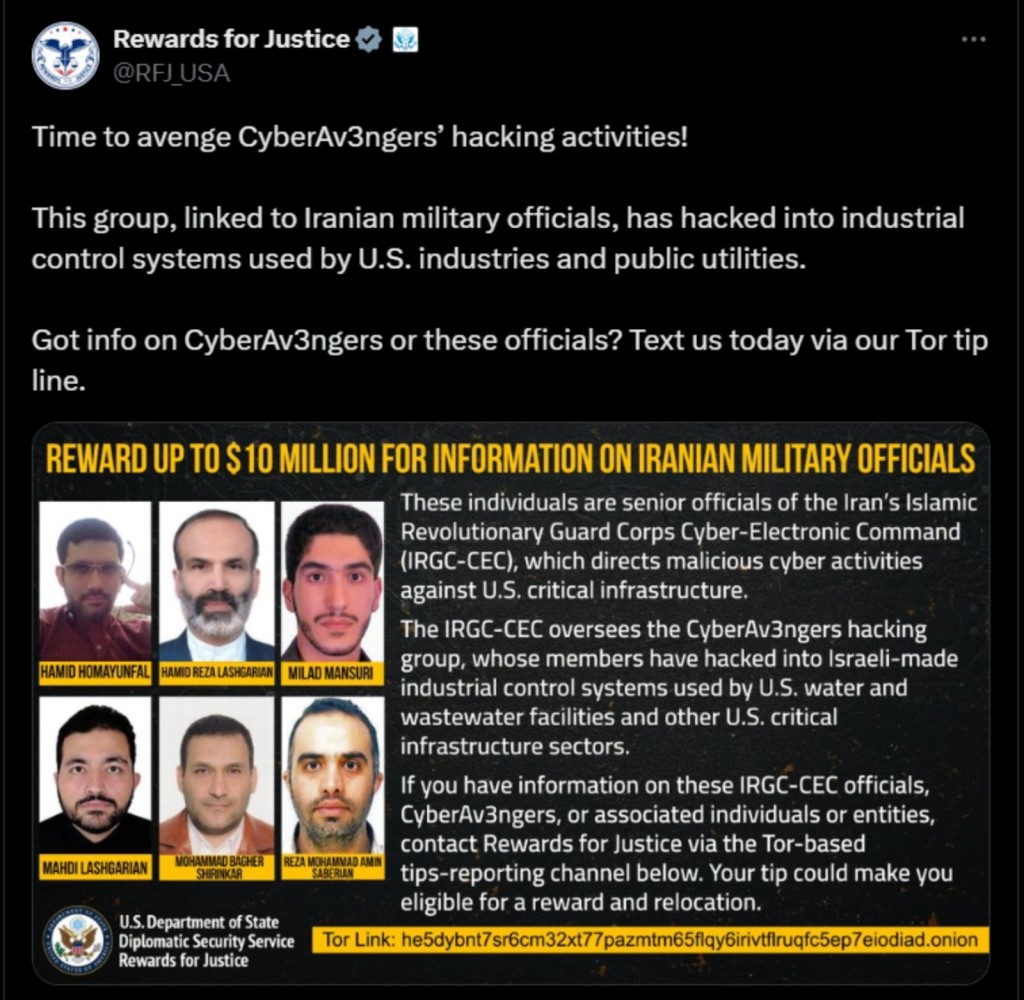
The U.S. State Department identified six Iranian security officials linked to the Iran-based Islamic Revolutionary Guard Corps (IRGC) group, reportedly responsible for the cyberattacks on U.S. water utilities in 2023, and is offering a $10 million reward via the Rewards for Justice program for information leading to the identification or location of these individuals.
Hamid Reza Lashgarian, Hamid Homayunfal, Mahdi Lashgarian, Milad Mansuri, Mohammad Bagher Shirinkar, and Reza Mohammad Amin Saberian were sanctioned on February 2 and are connected to Iran’s Islamic Revolutionary Guard Corps (IRGC) and its Cyber-Electronic Command (IRGC-CEC).
Hamid Reza Lashgarian is the Head of the IRGC’s Cyber-Electronic Command and a commander in the IRGC-Qods Force, while the others are IRGC-CEC senior officials responsible for “executing cyber activities.” In the advisory, the individuals stand accused of compromising industrial control systems.
The CyberAv3ngers group, affiliated with the IRGC-CEC and Mahdi Lashgarian, specifically targeted the Vision series programmable logic controllers (PLCs) manufactured by Israel-based Unitronics, compromising them via a default credentials exploit.
These PLCs are widely used in industries like water and wastewater, energy, food and beverage, manufacturing, and healthcare.
The group claimed the attack on Israeli PLCs in October 2023 via their Telegram channel, ultimately compromising and destroying PLCs across the U.S. and leaving anti-Israel messages starting November 2023.
The Environmental Protection Agency warned in March that cyberattacks against water utilities across the U.S. are becoming more frequent and severe, urging for immediate security measures, as about 70% of utilities inspected by federal officials over the last year violated breach prevention standards.