A Batch of 1 Million Credit Cards Is Shared for Free on New Dark Web Carding Site
- A recently-launched carding platform is giving away one million cards for free as a promotion.
- The site features sets from around the world and also offers a powerful search engine.
- Roughly half of the cards offered are still good for exploitation as their owners don’t know they have been compromised.
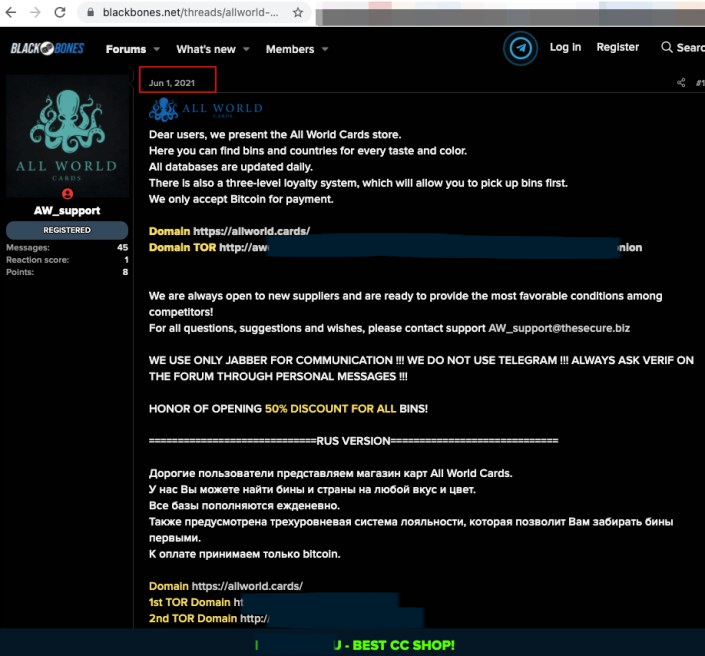
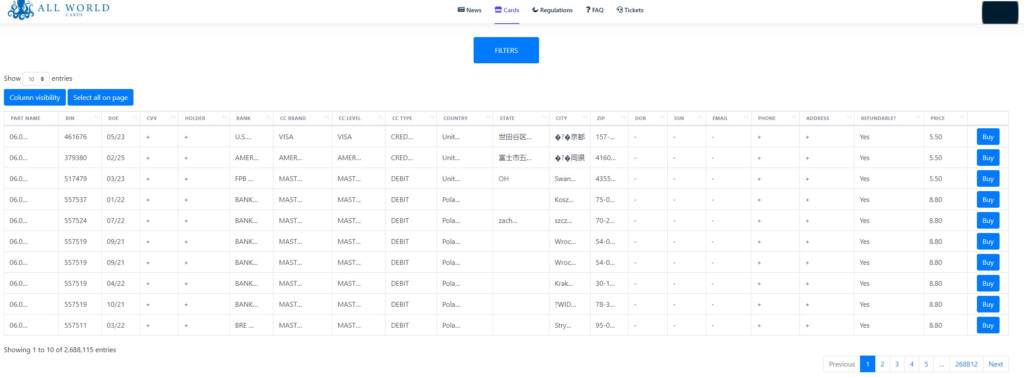
A new credit card dump has appeared on ‘AllWorld.cards’, a recently-launched dark web marketplace where cybercriminals buy, sell, or freely share goods of this kind, and it contains one million records including full holder names, expiration dates, the CVV number, and the owner’s address.
According to researchers of the d3lab, who analyzed the card pack, it appears to be a compilation of cards stolen from various sources like malware-infected PoS terminals deployed in petrol stations and supermarkets, as well as websites compromised by Magecart skimmers.
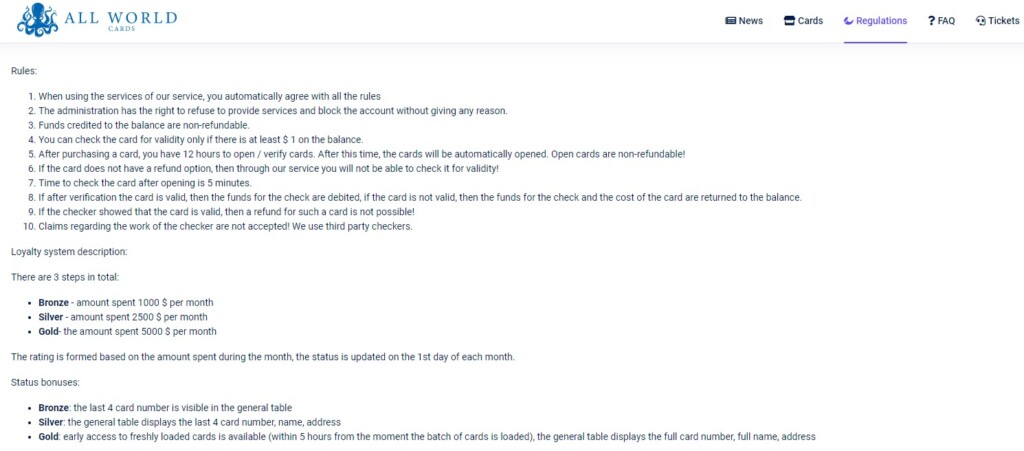
The particular set has been advertised on various dark web forums since the beginning of June. It is offered for free to promote AllWorld.cards, which is a relatively new marketplace that was registered in May 2021. The site only accepts Bitcoin for payment, and cybercriminals can only use Jabber to contact the sellers, while everything else on the platform is currently offered at a 50% discount. The site also follows a three-level loyalty system that prioritizes returning buyers so that they can exploit fresh packs before other members access the data.
More specifically, users who spend $5,000 or more on the site get the “Gold” level status and are given early access to freshly loaded cards within 5 hours from their upload on the site. “Silver” and “Bronze” users won’t even see the full card number and will be given 12 hours to verify what they got or ask for a refund. Anything credited to the balance cannot be touched, and the site declared trust to its own third-party checkers, so no tricks can be played there.
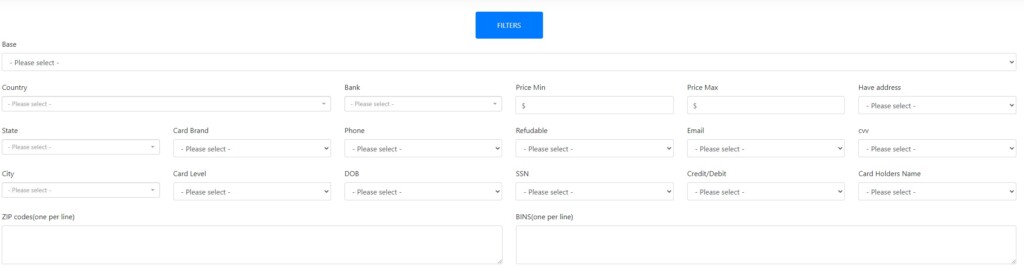
We have looked into some of the offerings on the site, and there’s really a plethora of listings from around the world. The price for each card ranges between $5.5 and $9.9, at least from what we were able to check. There is also a powerful search filtering system that offers quite a few options for crooks to narrow down their results and locate what they’re after quickly.
Back to the 1,000,000 cards offering, d3lab has made a bulk analysis of the pack and believes that roughly 50% are still operational and exploitable, as they have not been reported as stolen/compromised to the financial institutes that issued them. The researchers have sent notifications to the affected banks, but taking the appropriate action may take a while.