Threat Actors Exploit Known Oracle WebLogic Server Flaws for Crypto Mining
- 8220 Gang conducts a cryptocurrency mining operation leveraging known security flaws in the Oracle WebLogic Server.
- The multi-stage loading technique includes a first-stage loader impersonating the legitimate VPN application WireGuard.
- Fileless execution techniques evade disk-based detection mechanisms, and a PowerShell script deploys the XMRig cryptocurrency miner.
The 8220 Gang threat actor, which Trend Micro security researchers track as Water Sigbin, conducts a cryptocurrency mining operation exploiting known security flaws in the Oracle WebLogic Server, such as CVE-2017-3506, CVE- 2017-10271, and CVE-2023-21839 for initial access, and deploys cryptocurrency miners via PowerShell scripts.
Trend Micro researchers say the cybercriminal group manages to sidestep disk-based detection mechanisms by employing execution techniques such as DLL reflective and process injection to run the malware code solely in memory.
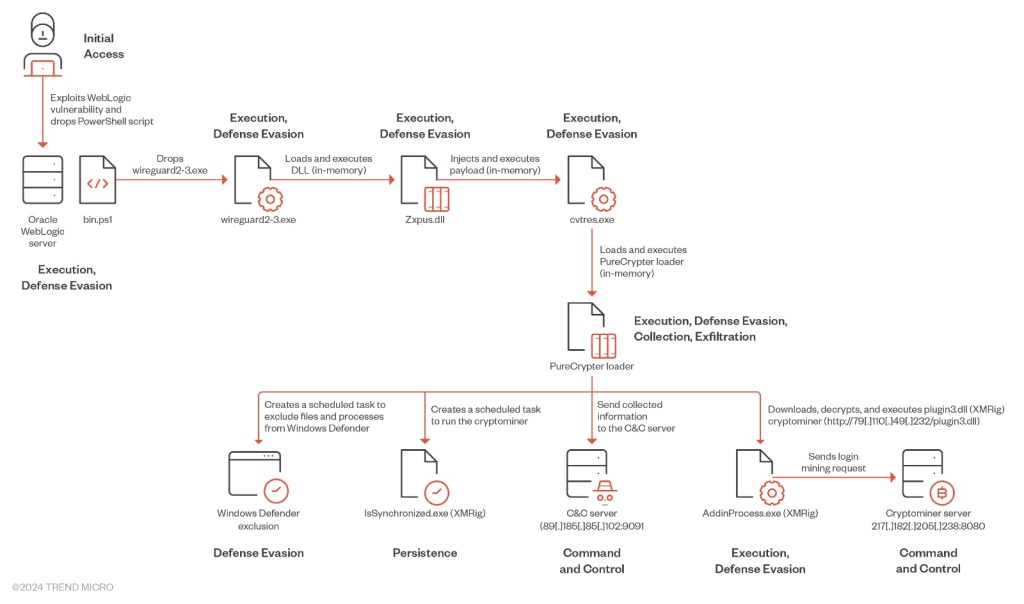
The 8220 Gang employs a multi-stage loading technique to deliver the PureCrypter loader and XMRIG crypto miner while protecting all payloads with .Net Reactor, a .NET code protection software against reverse engineering.
Exploiting CVE-2017-3506, the threat actor deploys a PowerShell script on the compromised machine and uses reflective DLL injection for in-memory execution to enhance the malware’s ability to evade detection.
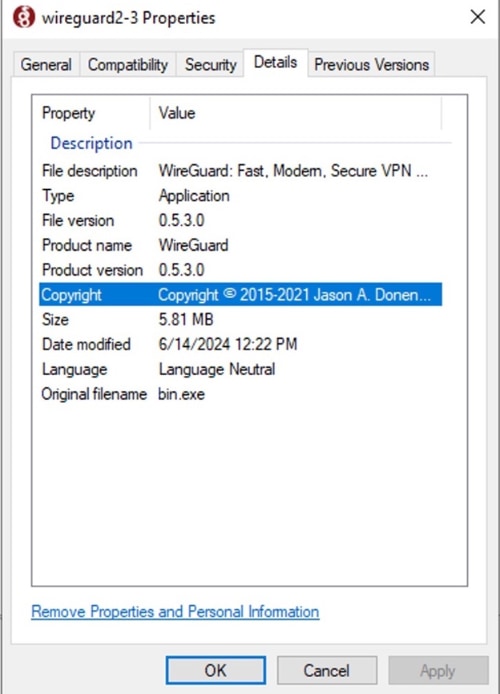
It drops a first-stage loader impersonating the legitimate VPN application WireGuard ("wireguard2-3.exe"). This is a trojan loader that executes a second-stage payload in memory, which executes another binary that resolves to a DLL trojan loader.
The DLL retrieves a binary named Vewijfiv that it decrypts via AES encryption with a specified key and IV and decompresses with GZip. Then, the loader creates a new process that mimics a legitimate one in “C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe” to load the next stage payload into memory.
The PureCrypter loader version V6.0.7D is the final DLL payload, which connects the victim’s machine with the malicious command-and-control (C2) server and downloads the final payload, which includes the XMRig cryptocurrency miner.
The malware can create a scheduled task under the Microsoft\Windows\Name folder with the highest privilege configured to run 15 seconds after creation followed by random intervals of approximately 6 minutes, then upon system startup or user login.
It also replicates itself as a hidden file named IsSynchronized.exe under the hidden path “C:\Users\$USERNAME$\AppData\Roaming\Name\” and can create a hidden scheduled task with a random name executing a PowerShell command to add malware files and processes to the Windows Defender's exclusion list.
Cybersecurity experts recommend using strong authentication methods such as multi-factor authentication (MFA) and regularly scaning networks and systems for vulnerabilities.