Suspected Chinese Hacker Group Used Open-Source Rootkits for Espionage
- Cyberespionage actor tracked as UNC3886 employed public rootkits to establish persistence in the targeted organizations.
- They deployed custom malware to extract credentials that aided lateral movement.
- Authentic third-party services were leveraged for malicious remote control inside the victims’ networks.
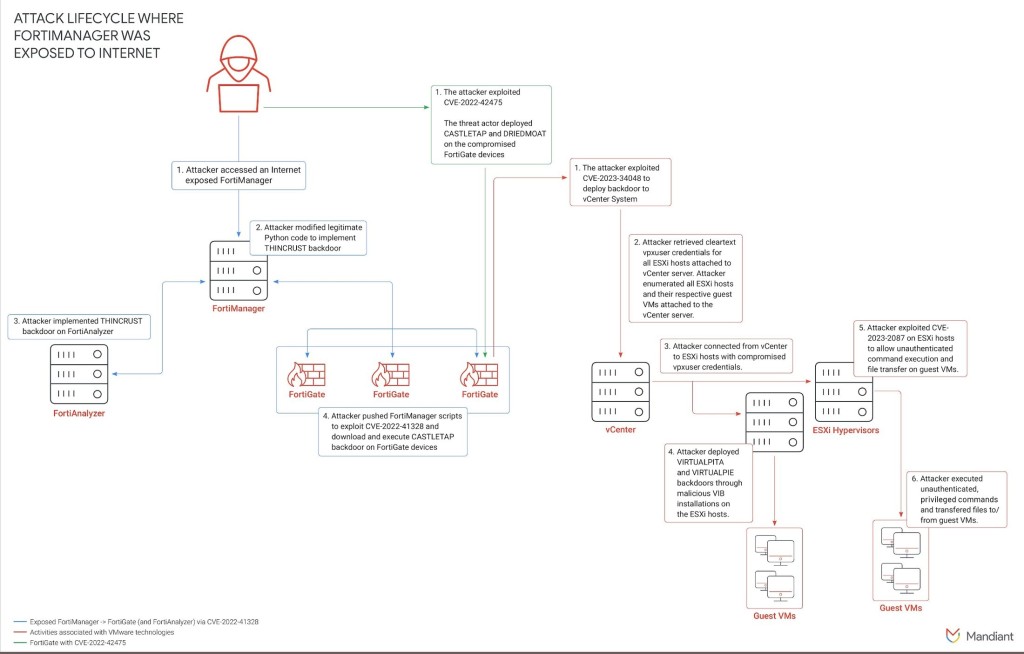
A suspected China-nexus cyberespionage actor that has targeted prominent strategic organizations globally was observed using publicly available rootkits for long-term persistence to deploy malware that leveraged trusted third-party services for command-and-control (C2), as per a new Mandiant report.
Tracked as UNC3886, the cybercriminal group gained unauthorized access and collected credentials with Secure Shell (SSH) backdoors, which were extracted from TACACS+ authentication via custom malware.
A now-patched vulnerability, CVE-2022-42475, in FortiOS's Secure Sockets Layer (SSL) VPN allowed arbitrary code or command execution from a remote unauthenticated attacker, reported in January 2023. A custom malware ecosystem on affected Fortinet devices analyzed in March 2023 showed compromised VMware technologies permitted full control of guest virtual machines due to zero-days offering access to vCenter servers and, subsequently, ESXi servers.
To maintain access and evade detection, the cybercriminals leveraged publicly available rootkits REPTILE and MEDUSA, an open-source rootkit implementing dynamic linker hijacking via LD_PRELOAD, on the guest virtual machines. MEDUSA can locally or remotely log user credentials from successful authentications and command executions, permitting lateral movement via valid credentials.
The threat actor deployed MOPSLED and RIFLESPINE, malware that uses rootkits for persistence and leverages authentic third parties like GitHub and Google Drive as C2 channels. MOPSLED is a shellcode-based modular backdoor that retrieves plugins from the C2 server using custom ChaCha20 encryption. RIFLESPINE is a cross-platform backdoor that transfers files and executes commands via Google Drive, using the CryptoPP library to implement AES encryption.
Researchers observed malicious activities on a TACACS+ server, an enhanced and more robust version of the original TACACS network protocol used for centralized authentication, authorization, and accounting (AAA) service.
The threat actor targeted the TACACS server via a C sniffer that processes TACACS+ authentication packets, performs decryption, and writes its contents to a specified file path called LOOKOVER, which uses the publicly available libpcap library.
Mandiant published detection and hardening guidelines for ESXi hypervisors and attack techniques employed by UNC3886, while Google SecOps Enterprise+ customers should check their Emerging Threats rule pack.