Rietspoof Malware Distribution on the Rise Through Skype and Messenger
- Rietspoof is currently getting daily updates, while infection rates are on the rise.
- The new “dropper malware” is now more sophisticated, more versatile, and more obfuscated than ever before.
- Analysts warn that Rietspoof is already hard to detect and stop by antivirus tools, and the situation may get worse with future versions.
Avast researchers have been tracking a new malware family that they named “Rietspoof” for the past month, and they warn users of Facebook Messenger and Skype that its spreading is on the rise. The particular malware was actually first spotted back in last summer, but it has now been optimized and deemed ready to reach the masses, getting used by numerous threat actors since the start of the year. The particular malware is considered a “dropper”, so it was created to download aggressive ransomware to the infected device, so it doesn’t do the damage on its own.
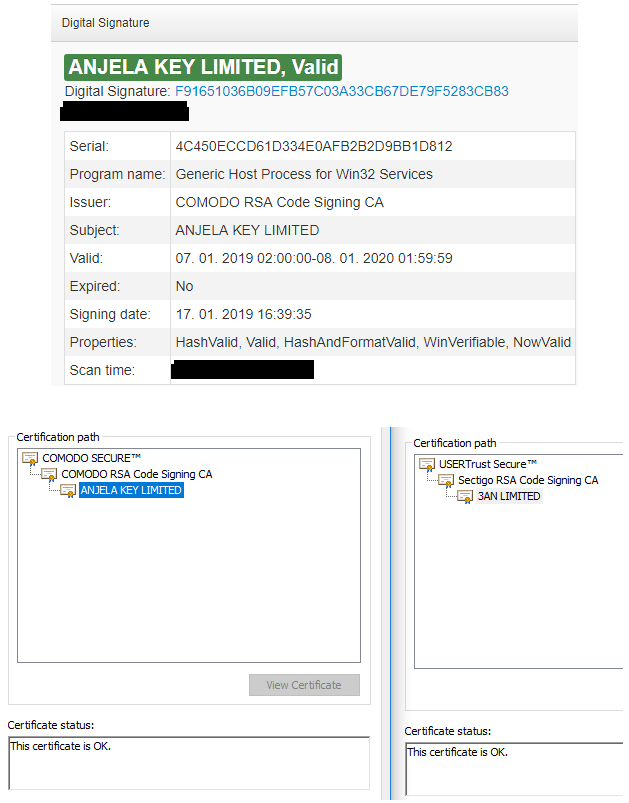
Avast warns about the versatility and resilience of Rietspoof, while they also note that the malware is currently getting daily updates, which means that it is getting more powerful and menacing day by day. Rietspoof is delivered through instant messaging clients like Skype or Facebook Messenger as an obfuscated Visual Basic Script inside a CAB file. This contains an executable that is digitally signed with a valid signature, making it immune to antivirus and antimalware scans of the Windows Startup folder. Thus, the malware is running free, deleting the CAB file after the executable binary is expanded and ran, and then starts communications with the C&C server.
source: blog.avast.com
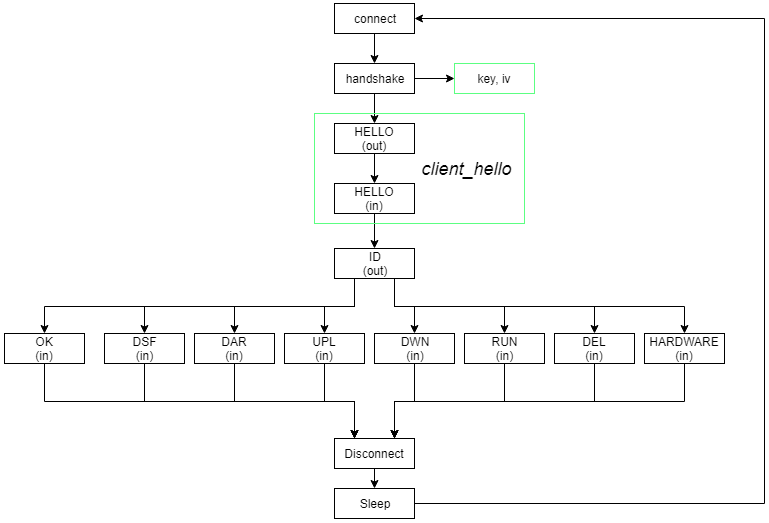
After further analysis, Avast researchers have figured out that the command and control server takes into account the IP of the infected machine in order to proceed further. Testing a US-based IP did initiate the next stage which comprises of various communication steps that concern system information gathering and sending, while the main payload downloading occurs in the final fourth stage. The researchers have tested several samples, seeing variations in the communication protocols, and a set of six commands that are sent from the C&C to the Rietspoof.
source: blog.avast.com
The security researchers warn that this new malware is under very active development and is quickly getting smarter and more versatile. The stage 3 communication protocol seems to have changed several times since last summer, seeking its maximum optimization and performance. Moreover, the team warns that they may have missed samples that are distributed to other IP address ranges or showcase a more specified targeting. Right now, users of messaging and chat apps are advised to be extra careful, as Rietspoof developers and distributors currently have their foot on the throttle.
Do you have any comments to make on the above? Share your thoughts in the comments section below, and don’t forget that you can always check out our social media community on Facebook and Twitter.