Hackers Increasingly Exploit YouTube Channels for Crypto Scams and Info-Stealing Malware
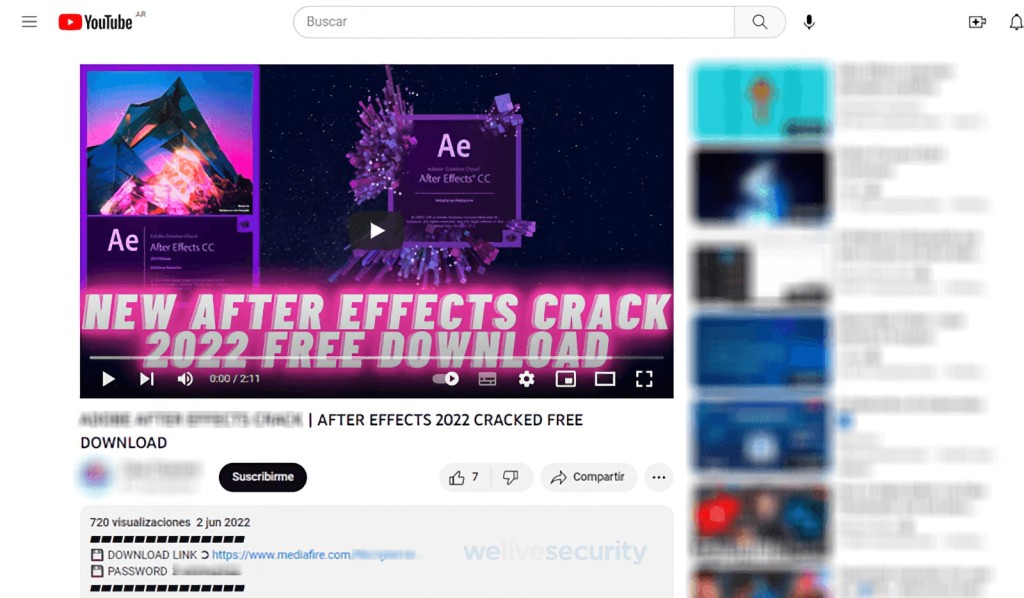
- Cybercriminals create fake tutorials about popular software like After Effects or ads for crypto giveaways.
- Sometimes they steal and repurpose YouTube channels to spread scams and info-stealing malware like Vidar.
- Their method of acquiring authentic YouTube login details relies on phishing emails and previously exposed credentials.
Cybercriminals are manifesting an increased interest in YouTube, security researchers say. They use lures such as ads for crypto giveaways and videos that appear to be tutorials for popular software, which include a link to a website for downloads that hide various info-stealing malware. Attackers also use apparently legitimate email messages for phishing.
Hackers resort to phishing campaigns to steal popular YouTube channels, which rely on the fake websites they create and the emails they craft to look like they are from YouTube or Google. These emails use sponsorship or collaboration deals as the lure and include attachments or links to files that allegedly contain further information, contracts, or terms and conditions.
In one example, a phishing email sent to a YouTuber delivered malware that deleted the user’s browser cookies. This forced the user to re-enter their login credentials, which are sent to the attacker after the victim submits them.
Repurposed channels are used to promote various scams, including crypto-related ones, and spread a wide array of info-stealing malware. Their descriptions often include URLs to pirated and malware-ridden software, movies, and game cheats.
The AhnLab Security Intelligence Center (ASEC) last month published a report highlighting a growing number of popular YouTube channel hijacks to distribute malware such as RedLine Stealer, Vidar Stealer, and Lumma Stealer.
These info-stealing malware strains among the ones are linked to countless cyberattacks, including the stolen credentials related to the Snowflake customers' breached accounts, unique social engineering campaigns, and Scattered Spider’s cybercriminal activities.
Lumma is used to steal crypto wallets, login credentials, 2FA browser extensions, and information from compromised machines. These stealers often pose as cheating software or video game cracks.
Researchers say criminals also hijack existing Google accounts and immediately post thousands of videos with info-stealing malware links. If the infection is successful, these malicious strains sometimes also steal other victim accounts, such as Instagram, Facebook, X, Twitch, and Steam.
Gaining access is even easier when target accounts are not protected by two-factor authentication (2FA), which YouTube creators have needed to use on their associated Google account since late 2021, but attackers can also circumvent 2FA additional security checks via stolen session cookies from the victims’ browsers.
Of course, it’s a known fact that attackers use credentials from past data breaches to gain unauthorized access to existing accounts or use automated tools to try numerous password combinations in brute-force attacks.